Introduction
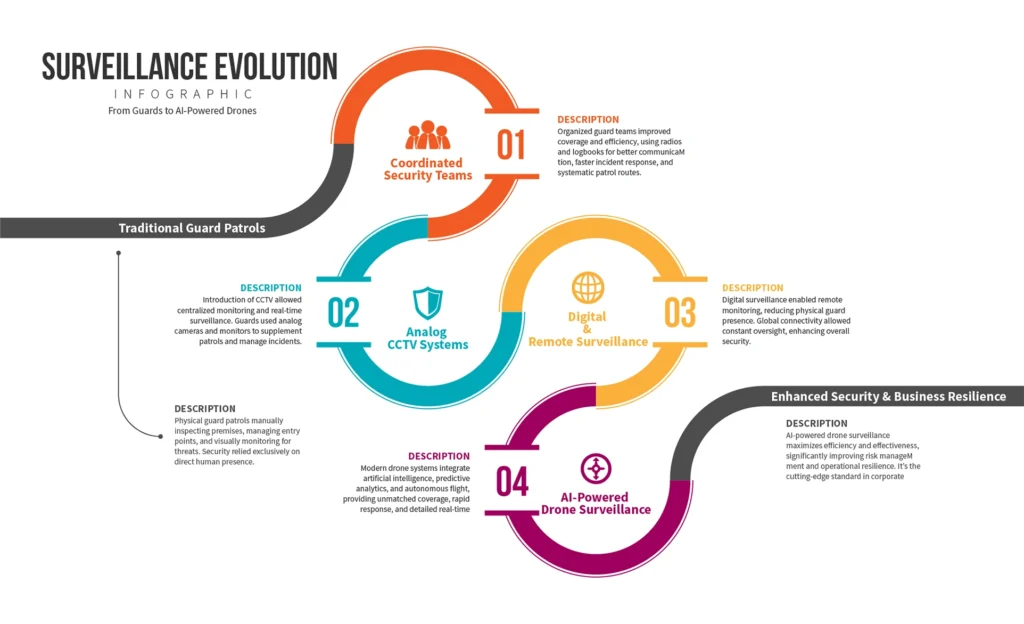
In an era defined by rapid technological advancement, drone technology has dramatically transformed corporate security capabilities. Unmanned aerial vehicles (UAVs) – commonly known as drones – now serve as agile “eyes in the sky,” providing surveillance coverage and response capabilities that were unimaginable with traditional guards and fixed cameras. Unlike static CCTV cameras or patrol routes limited by human endurance, drones can autonomously roam across vast facilities, zoom in on details from hundreds of feet above, and relay real-time video to security teams. This evolution marks a paradigm shift: organizations are moving from reactive security postures to proactive, technology-driven strategies. For instance, businesses that blended drones with conventional measures have seen up to a 30–40% reduction in security incidents and 60% cost savings compared to guard-only programs (Drone Industry Visionary Interview: Ryan Smith defines the tangible (and invisible) ROI of drone security | Commercial UAV News). Such results underscore how aerial surveillance isn’t just a novel gadget – it’s a force multiplier for corporate security.
Traditional security methods – locked doors, alarm systems, guard patrols, and CCTV networks – will always have their place. However, they also have inherent limitations. Fixed cameras cover only their line of sight, leaving blind spots; guards on foot or in vehicles can be in only one place at a time and may take precious minutes to respond to far-flung incidents. By contrast, drone surveillance offers unmatched agility and reach. A single drone can patrol an area that would otherwise require multiple cameras or roving guards, eliminating blind spots and reducing response time to mere seconds (Cost-Effective Security: Comparing Drone Security to Traditional Methods) (Cost-Effective Security: Comparing Drone Security to Traditional Methods). Modern security drones come equipped with high-definition day/night cameras and thermal imaging, acting as ever-vigilant sentinels that can detect movement in dark or hard-to-access areas. They provide a bird’s-eye view of assets and perimeters, which is invaluable for monitoring large campuses, industrial sites, and events (Navigating Modern Security Challenges: The Crucial Role of Physical and Surveillance Security Solutions – Cuneo Consulting). In effect, drones extend the perimeter of awareness far beyond the fences – they are the unblinking eyes that can continuously watch over corporate interests from above.
Equally important is how drone surveillance enables a proactive security posture. Rather than waiting for an alarm to sound or a breach to be discovered after the fact, drones can conduct regular patrols and respond instantaneously to triggers. For example, if an intrusion sensor trips at a remote corner of a facility at 2 AM, a drone can be dispatched immediately to investigate, potentially spotlighting an intruder within moments – long before a guard could ever arrive. This rapid verification not only helps intercept threats in progress, but also drastically cuts down on false alarms (since the drone’s feed can confirm whether an intrusion is real or just a stray animal). By contrast with traditional methods, which often involve after-the-fact review of camera footage or laborious guard tours, drones facilitate real-time, intelligence-driven security. They act as a deterrent (an intruder who sees a drone overhead is likely to flee) and as a frontline response tool that guides ground teams more effectively. In short, a modern corporate security strategy that integrates drones is far more dynamic and preventive than one relying solely on static measures.
It’s no surprise, then, that corporate adoption of security drones is accelerating. The global surveillance drone market is booming – projected to reach around $5.5 billion in 2023 with annual growth over 14% going forward (Surveillance Drone Market Size & Share | Growth By 2034 – Fact.MR). What was once bleeding-edge technology restricted to military or government use is now an accessible business tool. From Fortune 500 corporate campuses to mid-sized industrial parks, organizations are embracing drones to protect assets and people. Early adopters have demonstrated clear returns on investment (ROI) and competitive advantages: better loss prevention, improved safety, and often lower operational costs. Executives are taking note that drone surveillance is not just a security expense, but a strategic investment. It yields tangible benefits like reduced theft and vandalism, improved incident response, and enhanced situational awareness for management. As a result, drone overflights of corporate rooftops and perimeters are increasingly as routine as morning badge swipes at the front door.
This comprehensive article serves as a definitive resource on “Drone Surveillance for Corporate Security.” It will guide you through every aspect of adopting and leveraging drones as part of a modern security program – from the high-level strategic rationale down to the technical nuts-and-bolts and regulatory checkpoints. We begin by examining the strategic and operational imperatives driving drone deployment in corporate security, including ROI analyses and executive-level benefits. Then, we dive deep into drone technology – exploring platform types, sensors (payloads), performance metrics, and maintenance considerations that Security Directors must understand. We’ll explore core applications and sector-specific use cases, illustrating how drones are applied in industries ranging from logistics and critical infrastructure to corporate campuses and retail. Next, we discuss strategies for seamless integration of drones into your existing security ecosystem – ensuring your aerial assets work in tandem with video management systems, access control, and alarm monitoring. We also tackle the vital topics of regulatory compliance and ethics – navigating FAA rules, privacy concerns, and insurance requirements to deploy drones lawfully and responsibly. For those ready to implement, we provide a step-by-step blueprint for developing a corporate drone program, covering everything from pilot training to standard operating procedures (SOPs) and performance monitoring. Finally, we cast an eye to the future in emerging trends, such as AI-driven autonomy, drone swarms, and counter-drone defenses, so you can future-proof your security strategy.
By the end of this guide, C-suite executives, Security Directors, Compliance Officers, and Operations Managers will have a 360-degree understanding of how to integrate drone surveillance into corporate security – and why doing so is fast becoming indispensable for advanced protection. Drone surveillance is more than a buzzword; it’s a game-changing component of proactive security that can safeguard your organization in ways previously unattainable. The “unblinking eye” of a drone never tires, never blinks, and never looks the wrong way – providing continuous vigilance over what matters most.
The Strategic & Operational Imperative for Drone Surveillance
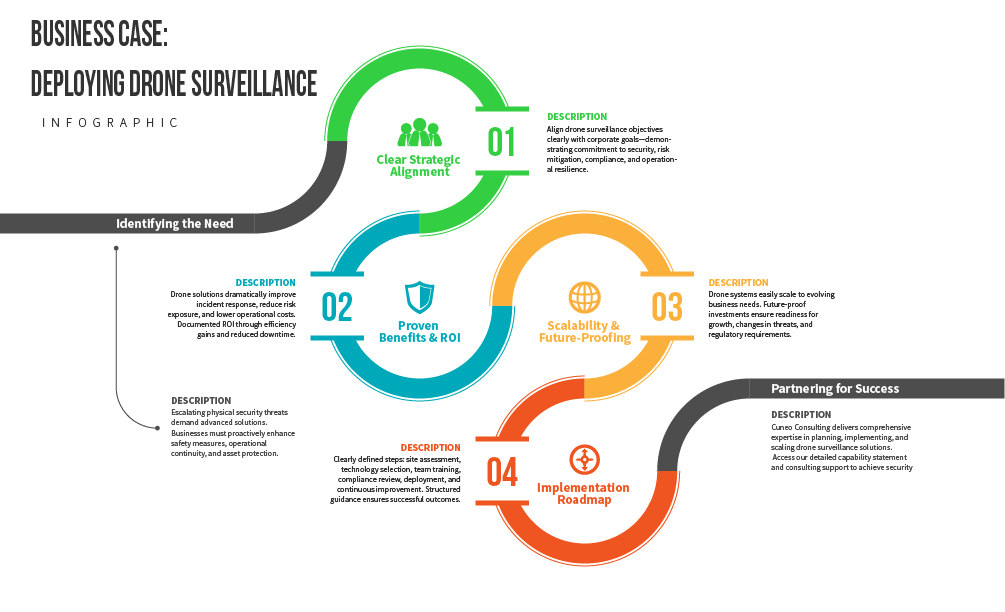
Why have drones so quickly moved from novelty gadgets to must-have corporate security tools? This section explores the strategic and operational drivers behind the imperative to adopt drone surveillance today. In a climate of evolving threats, cost pressures, and technological opportunities, drones offer a compelling value proposition. We will examine the business case – including return on investment (ROI) and total cost of ownership (TCO) – and compare drone-based security to traditional methods like staffed patrols and static cameras. The goal is to articulate why investing in drone surveillance makes sense at the executive level, and how it can yield dividends in security effectiveness and efficiency.
Evolving Threats Demand Proactive Surveillance
Modern enterprises face a more complex threat landscape than ever. Corporate campuses, distribution centers, and industrial facilities must contend with risks ranging from organized theft rings and espionage to vandalism and workplace violence. Traditional security measures alone (fences, alarms, guards) are often insufficient to deter or respond to these advanced threats. Drones fill critical gaps by providing rapid, flexible coverage. Aerial surveillance is essentially omnipresent and omnidirectional – drones can see over and around obstacles, giving security teams insight into areas that adversaries might exploit. For example, during the 2023 Boston Marathon (a high-threat public event), authorities employed drone surveillance to cover zones that ground police could not easily see, helping ensure an incident-free environment (Navigating Modern Security Challenges: The Crucial Role of Physical and Surveillance Security Solutions – Cuneo Consulting). This kind of capability is directly transferable to corporate settings: a drone can watch a perimeter fence line or a parking lot from above, detecting intruders or suspicious vehicles that would escape notice from the ground.
Moreover, the mere presence of visible security drones can alter the behavior of potential wrongdoers. Much like the deterrence effect of security cameras (often cited as reducing theft by significant percentages), drones up the ante – they are mobile, unpredictable, and can follow an intruder in a way a fixed camera cannot. Would-be trespassers or thieves recognize that once a drone locks onto them, hiding or escaping becomes far more difficult. This psychological deterrent is a new arrow in the corporate security quiver, contributing to a more hardened target. In essence, drones raise the cost and risk for adversaries, thereby lowering the likelihood of security incidents.
Demonstrable ROI for Businesses of All Sizes
Cost is a constant concern in corporate security management. Executives need to justify expenditures by showing improvements to the bottom line, either through loss prevention or operational savings. Here, drone surveillance makes a powerful financial case. While drones do require upfront investment and ongoing maintenance, they often enable significant cost efficiencies when compared to traditional methods. Consider the labor costs of manned security: a single full-time security officer (with salary, benefits, training) can cost $50,000–$70,000 per year or more. Yet one officer can patrol only a limited area. To secure a large facility 24/7, many officers are needed, driving personnel costs into the hundreds of thousands. Cameras are cheaper long-term but have high installation costs per location and still require personnel to monitor. Drones, by contrast, can reduce the need for multiple guards and cameras by covering their duties with one device. After an initial purchase or lease, a drone’s operating cost is mainly electricity and periodic maintenance – minimal compared to a human salary.
Real-world examples underscore this ROI. Titan Protection, a U.S. security firm, pioneered a “blended” approach using drones to augment its guard services. The result was a 60% reduction in security labor costs for clients and a simultaneous drop in incidents by 30–40% (Drone Industry Visionary Interview: Ryan Smith defines the tangible (and invisible) ROI of drone security | Commercial UAV News). In other words, drones made security not only more effective but also more economical. Many companies are discovering similar economics. In one industry survey, 92% of companies using drones reported seeing ROI within one year of deployment (Security Drones: Benefits, Use Cases and ROI of Using Drones in the Security Industry). Savings come from multiple avenues: reduced theft losses (thanks to better deterrence and quick response), lower headcount or overtime for security staff, fewer false alarms and associated disruption, and possibly even lower insurance premiums. For instance, a manufacturing company that suffered frequent after-hours break-ins might invest in a drone patrol program. If theft losses drop by $200,000 in the first year (due to intruders being scared off or caught by drones) while program costs are $100,000, that’s a clear net positive ROI – and improved safety to boot.
ROI analysis should also consider avoided costs. A single major security breach – such as a theft of valuable intellectual property or a safety incident due to an undetected intruder – can cost millions in damage, legal claims, and reputational harm. Drones act as an insurance policy against such catastrophic events. It’s hard to measure the exact dollar value of an incident that didn’t happen because a drone was watching, but preventing one serious incident can itself justify the investment many times over.
From small businesses to large enterprises, the scalability of drone programs means the model can fit various budgets. A small business (say a regional warehouse or a data center) might start with one affordable drone and a part-time pilot, focusing on the highest-risk times (night and weekends). Even this limited use can yield outsized benefits by catching that one critical incident or providing valuable situational awareness during an emergency. Mid-sized companies could opt for a fleet of drones on rotational patrol, significantly extending their security reach without multiplying staff. Global corporations are beginning to implement enterprise drone programs across multiple sites, coordinated through a central command center – a concept that promises economy of scale and standardized protection. The key is that drones are modular and flexible: you can deploy as few or as many as needed, and add more units as your operations grow or risks change.
Drone Surveillance TCO Calculator
Traditional Security Costs
Drone Surveillance Program Costs
TCO Comparison Results
Traditional Security Costs
Drone Program Costs
Return on Investment
Total Cost of Ownership Considerations
While ROI highlights the benefits, decision-makers must also weigh the Total Cost of Ownership (TCO) for drone surveillance. TCO includes not just the purchase price of drones, but all ongoing costs: maintenance, battery replacements, software subscriptions, pilot training, regulatory compliance efforts, insurance, etc. Fortunately, drones tend to have favorable TCO profiles when planned carefully. Quality commercial-grade security drones can range from $5,000 to $50,000 each depending on capabilities. Additional equipment might include spare batteries, charging stations, controller devices, perhaps a drone “dock” or hangar if using automated launch systems. On the operational side, you need licensed pilots (which could be existing security staff cross-trained, or external service providers), and those pilots will need periodic refresher training and certification renewal. Maintenance involves routine checks, firmware updates, part replacements (propellers, motors) and occasional repairs.
When spread over the lifespan of the equipment (typically 3–5 years for intensive use, though many drone airframes can last longer with upgrades), these costs often come out lower than equivalent human patrol costs over the same period. For example, the annual maintenance and support cost for a drone might be a few thousand dollars – trivial next to a full-time guard’s yearly wages. One analysis by a security integrator found that once deployed, a single drone can effectively cover areas that would require 3–4 security guards or dozens of CCTV cameras, but at a fraction of the ongoing cost (Cost-Effective Security: Comparing Drone Security to Traditional Methods) (Cost-Effective Security: Comparing Drone Security to Traditional Methods). The cost to scale up is also low – adding a new drone to cover expanded operations doesn’t require constructing new guard posts or extensive infrastructure; it’s a matter of purchasing another unit and integrating it. As a result, drones offer near-linear scalability: doubling your coverage with drones might roughly double your costs (plus modest training additions), whereas doubling coverage with guards could more than double costs when you factor in management, shift overlaps, etc. (Cost-Effective Security: Comparing Drone Security to Traditional Methods) (Cost-Effective Security: Comparing Drone Security to Traditional Methods). This scalability is extremely attractive for growing businesses or those with fluctuating security needs (for instance, a company that needs extra surveillance only during certain high-risk projects or seasons can deploy more drones temporarily).
TCO calculations should include software and data costs as well. Many drone systems require subscriptions to management software or data storage for recorded footage. However, these software platforms often bring powerful features like automated flight planning, AI analytics, and cloud backup that significantly enhance the value of the drones. Executives evaluating TCO should ask vendors about package deals or enterprise licensing that can cover multiple drones under one plan. Additionally, working with an experienced security consultant can help in planning a cost-effective deployment – avoiding common pitfalls that lead to hidden costs. For instance, buying consumer-grade drones might save money upfront but could lead to higher failure rates and replacements (a classic false economy). Investing in enterprise-grade drones and robust integration yields better long-term reliability – an important TCO consideration.
In summary, when viewed over a multi-year horizon, the TCO of a well-implemented drone surveillance program is highly competitive. The combination of reduced labor expenses, scalable expansion, and prevention of costly incidents contributes to a compelling business case. Companies should perform a detailed cost-benefit analysis, but in many scenarios the numbers favor drones, especially when intangible benefits (like improved safety culture and stakeholder confidence) are factored in.
Drones vs. Traditional Security Methods
To fully appreciate the strategic imperative of drone surveillance, it’s helpful to directly compare drones with the traditional security methods they augment or replace: namely, human guards and fixed surveillance cameras. Each approach has strengths; the goal is to understand where drones excel and how they can fill the gaps of conventional measures.
- Coverage and Visibility: Traditional cameras are stationary – they provide a continuous watch but only in a fixed field of view. Guards can move, but their vantage point is limited to ground level. Drones combine the best of both: continuous surveillance with mobility. A single drone at 200 feet altitude can surveil an area that would require many static cameras to cover, and it can reposition on demand to track movement or eliminate blind spots (Cost-Effective Security: Comparing Drone Security to Traditional Methods) (Cost-Effective Security: Comparing Drone Security to Traditional Methods). Unlike a guard who might have to walk around a building to see behind it, a drone can simply fly over in seconds. In effect, drones blanket your facility with an on-demand aerial mesh of visibility, greatly reducing blind areas. Traditional methods struggle with complex terrain (hills, dense equipment yards, etc.), whereas drones literally rise above the challenge.
- Responsiveness: When an incident occurs, time is critical. A guard might take several minutes or more to reach a far corner of a property after an alarm. Police response times can be even longer. Cameras can record events, but they don’t move to follow a suspect – someone watching the feed must direct ground responders. Drones excel in speed of response. The moment an alarm triggers or suspicious activity is detected, a drone can be autonomously dispatched to that exact location, often arriving in under a minute – long before a person could. For example, if a fence sensor detects a breach, a drone can zip over and start streaming video of that spot, giving security a real-time assessment (Cost-Effective Security: Comparing Drone Security to Traditional Methods) (Cost-Effective Security: Comparing Drone Security to Traditional Methods). This rapid response can mean the difference between scaring off or catching an intruder versus arriving to find them long gone. In safety scenarios (say, a fire or chemical spill), drones can provide eyes on the scene far faster than any human, helping first responders with critical information. Traditional guards simply cannot match the reactive agility of drones.
- Endurance and Reliability: Human guards have limitations – they can become fatigued, distracted, or simply have a bad day. They also require breaks, shift changes, and management oversight. Cameras don’t fatigue, but their effectiveness can wane in bad weather or poor lighting unless they’re high-end models, and even then they might need auxiliary lighting. Drones can operate programmed patrols tirelessly and—when equipped appropriately—can see in darkness (thermal imaging) and aren’t impeded by most weather aside from extremes. While a drone’s battery life is finite (typically 20–40 minutes for many models), this is mitigated by using multiple drones in rotation or tethered drones for constant power. In essence, drones offer reliable, repeatable performance for routine surveillance tasks. They will never “nod off” during a dull midnight shift. With AI automation, they can also notify human operators only when something truly requires attention, increasing overall reliability of detection. Of course, drones do require human involvement for decision-making and maintenance, but they significantly reduce the mundane workload on security personnel, freeing staff to focus on analysis and action rather than walking endless rounds or staring at banks of monitors.
- Adaptability and Scalability: Security needs can change rapidly – perhaps a particular asset becomes high-value overnight, or a new construction project creates a temporary vulnerability. Traditional security is often slow to adapt (hiring new guards or installing new cameras takes time and money). Drones are extremely adaptable. Need extra eyes on the loading dock this week? Assign the drone more frequent passes there. Expansion of the facility? Simply extend the drone’s patrol route or add another drone to cover the new area. During special events (shareholder meeting, product launch party, etc.), drones can be deployed specifically for the duration of the event and then re-tasked elsewhere afterward. This flexible scaling is a strategic asset. According to security experts, adding more drones to a fleet is straightforward and doesn’t significantly disrupt existing infrastructure, whereas scaling guards or cameras involves substantial overhead (Cost-Effective Security: Comparing Drone Security to Traditional Methods) (Cost-Effective Security: Comparing Drone Security to Traditional Methods). Executives appreciate that drone programs can grow with the business or be reconfigured as threats evolve, protecting the investment over the long term.
- Capabilities: There are tasks simply beyond the capabilities of traditional methods. For example, thermal imaging from an aerial viewpoint can detect a hidden trespasser at night far more effectively than a flashlight-wielding guard or a night-vision CCTV. Drones can also be equipped with loudspeakers to issue warnings, something a camera certainly can’t do. In some cases, a drone might even be able to intervene (non-lethally) by sounding an alarm or spotlighting an intruder to disorient them. While guards have the advantage of physical intervention (drones can’t handcuff a suspect – at least not yet!), they often must find the suspect first, and that’s where drones tilt the scales. The ideal approach is blending the two: drones find, track, and illuminate the threat, while ground personnel intercept and apprehend – a symbiosis that vastly improves safety for the guards, who have much more information about what they’re walking into.
Of course, traditional methods still have their place. A drone won’t replace the reassurance of a friendly security officer greeting employees, nor can it perform tasks like badge checks or physically lock a door. Instead, drones enhance and focus human effectiveness. By taking over the monotonous patrols and the initial recon of any alarm, drones free up human guards to concentrate on tasks that require judgment, customer service, and physical intervention. The comparison isn’t drones or humans – it’s the optimal combination of drones, humans, and static systems to achieve the highest security level for the lowest cost.
From a strategic viewpoint, organizations that leverage drones are effectively arming their security teams with a powerful new tool that competitors or adversaries may lack. It’s akin to moving from horse-mounted watchmen to CCTV in the mid-20th century – those who adopted CCTV early gained a security edge. Today, drones are that edge, offering capabilities that set apart a cutting-edge corporate security program from a conventional one. In boardroom terms, deploying drones aligns with a forward-leaning risk management strategy and demonstrates innovation in protecting the company’s assets and people.
Executive-Level Benefits and Risk Mitigation
For C-suite executives and enterprise risk managers, drone surveillance offers benefits that resonate beyond the security department. One major advantage is holistic risk mitigation. Drones can reduce not only security risk (like theft or sabotage) but also safety and operational risks. They can quickly inspect facilities after natural disasters or accidents (identifying hazards before people enter), and they can monitor compliance (for example, checking that safety protocols are followed in remote yard areas). This contributes to business continuity and resiliency, protecting the company’s operations from disruptions. Seen in this light, the investment in drones is an investment in keeping the business running smoothly under adverse conditions – a clear executive concern.
Another benefit at the executive level is data and intelligence. Drones don’t just provide security; they collect valuable data that can be analyzed for insights. Patterns observed in drone surveillance might reveal, say, a recurring bottleneck in a facility’s traffic flow or an employee behavior that raises safety issues. Over time, drone footage and sensor readings can be mined (with the help of analytics software) to inform decisions outside of security – like facility planning or process improvements. In essence, a network of security drones doubles as a data acquisition tool for the enterprise, aligning with trends in big data and IoT (Internet of Things). A forward-thinking executive can leverage this for cross-departmental value.
From a governance and compliance perspective, deploying state-of-the-art security like drones also shows regulators, insurers, and investors that the company takes asset protection seriously. In some industries, having advanced surveillance might help demonstrate compliance with security requirements or industry standards (for instance, critical infrastructure sectors often have stringent surveillance mandates – drones can help meet them). There’s also an argument to be made that proactive drone use can reduce liability. If an incident does occur, the company can show it had robust measures in place; and drone footage can provide clear evidence of what happened, which might limit legal exposure. Many legal and insurance stakeholders increasingly see drones as part of best practices for facility security.
At the brand and reputational level, being known as an organization that employs cutting-edge security tech can bolster an image of innovation and safety. Clients, visitors, and employees may feel more secure knowing that the premises are monitored by advanced drones as well as guards. It sends a message: this company is serious about protection. Of course, messaging must be balanced with privacy (more on that in the compliance section), but generally, a well-communicated drone program can reassure stakeholders that the environment is under vigilant control. This is especially important for companies that invite clients on-site (like data centers showing their secure measures to customers, or manufacturers hosting auditors). A quick anecdote can illustrate: A large corporate campus in California implemented routine drone patrols and publicized it internally – within months, employee surveys noted improved feelings of safety on campus, as employees knew that if they worked late, a drone was circling the parking lots to watch over them. Happier, safer employees are certainly an executive-level benefit, contributing to talent retention and productivity.
In sum, the strategic imperative for drone surveillance in corporate security is clear. We have a confluence of factors – evolving threats, proven ROI, manageable TCO, superior capabilities, and broad organizational benefits – that make a compelling case. Forward-looking executives and security leaders recognize that continuing to rely solely on yesterday’s methods is a liability. Embracing drone technology is a way to future-proof the security strategy, gaining both quantitative and qualitative advantages. As we move to the next sections, keep in mind how these high-level motivations set the stage for the practical implementation: understanding the technology itself, applying it effectively, and integrating it seamlessly. The business case is the “why,” and it’s robust; next we delve into the “what and how” of drone systems that deliver on this promise.
Drone Technology Deep-Dive: Platforms, Payloads, and Performance
To successfully integrate drones into corporate security, one must understand the technology at a fundamental level. This section provides a deep dive into the nuts and bolts of security drone systems – the platforms (types of drones) available, the payloads (sensors and equipment) they carry, and key performance factors that determine what a given drone can do. We’ll compare different drone types (from nimble quadcopters to long-endurance fixed-wing models), explore the range of surveillance tools (cameras, thermal imagers, etc.) they can deploy, and discuss the practical aspects of keeping drones running reliably (maintenance, battery life, weather considerations). By the end of this section, Security Directors and technical managers will have a solid grasp of how to select the right drones for their needs and what operational trade-offs to expect.
Drone Platform Types: Finding the Right Fit
Not all drones are created equal – various platform designs exist, each with strengths tailored to particular use cases. The main platform categories to consider for corporate security are multirotor drones, fixed-wing drones, and hybrid VTOL drones. Understanding their differences is crucial in matching the tool to the task.
- Multirotor Drones (Quadcopters and more): The most common security drones are multirotors – often quadcopters (4 rotors) but also hexcopters or octocopters for heavier lift. These drones take off and land vertically, hover in place, and maneuver with precision. Key advantages: They excel at stationary observation and slow, deliberate movement. This makes them ideal for tasks like perimeter patrol (flying low and following a fence line) or zooming in to inspect a specific spot (a door left open or an unidentified object). They are generally easy to deploy and control, even in tight spaces, and can take off from a small patch of ground or a rooftop. Many security-focused drones on the market – such as the DJI Matrice series or the Autel Evo series – are multirotors. Modern multirotors typically offer flight times in the range of 20–40 minutes per battery, speeds up to 30–50 mph, and can carry moderate payloads (a high-resolution camera plus perhaps a loudspeaker or spotlight). Limitations: Their relatively short flight endurance means they either need frequent battery swaps or a rotation of units to maintain continuous coverage. They also have lower aerodynamic efficiency, so they’re not ideal for very long distance patrols (beyond, say, a couple of miles of total travel per flight). However, for most corporate campuses and facilities, multirotors provide ample coverage. Their ability to hover means they can also serve as “virtual tower cameras” – holding a high vantage point over an area of interest for extended periods (until the battery runs out). If constant overwatch is needed at a fixed spot, some companies use tethered multirotors – drones attached via a cable to a ground power source, allowing 24/7 flight (at the cost of being confined to the tether’s length radius). In summary, multirotors are versatile and user-friendly, suitable for the majority of security scenarios requiring up-close observation and agile response.
- Fixed-Wing Drones: These drones resemble small airplanes with wings. They need to move forward to generate lift (like a plane) and cannot hover in place. Key advantages: Fixed-wing drones have significantly longer flight times – often 1–2 hours or more on a battery or fuel cell, and they can cover great distances fast. This makes them valuable for extremely large properties or linear infrastructure. For example, a pipeline company or a sprawling industrial site (such as a 10,000-acre solar farm) might use a fixed-wing drone to routinely fly long surveillance routes. Fixed-wings are also more stable in strong winds and can reach higher altitudes and speeds (some can cruise at 60–100 mph). Limitations: They usually require either a runway/takeoff strip, a catapult launcher, or a parachute recovery system – which isn’t practical in many corporate environments. Some smaller fixed-wing drones can be hand-launched, but landing them without damage can be tricky without a runway or net. Crucially, since they can’t hover, fixed-wings are not suited to loiter over a spot or navigate within tight confines (e.g., around buildings or courtyards). Their surveillance style is more like a constant broad sweep. Imagine a fixed-wing doing continuous loops around a facility’s perimeter – great for general oversight, but if an incident is detected, a multirotor might still be needed to hover and closely monitor the situation. Fixed-wings also often carry lighter payloads (due to the need to stay aerodynamic). They might have a camera but usually less payload flexibility than a multirotor. In corporate security, fixed-wing drones are somewhat niche – used when very large area coverage and endurance are top priority, and usually in rural or expansive campus settings where launch/landing is manageable.
- Hybrid VTOL (Vertical Takeoff and Landing) Drones: Bridging the gap between the above types, hybrid VTOL drones have the features of both multirotors and fixed-wings. They might have rotors that tilt or separate lift and thrust systems – allowing them to take off vertically like a helicopter, then transition to winged flight for efficient cruising. Key advantages: VTOL hybrids offer hover capability along with extended range. This can be a game-changer for certain applications – for instance, a security drone that can launch from a parking lot, fly 10 miles of fence line, then stop and hover to zoom in on a detected anomaly. Several emerging security drone platforms use VTOL designs to enable autonomous coverage of large perimeters without the infrastructure of runways. Flight time on hybrids typically falls between multirotors and fixed-wings (perhaps 45–60 minutes), and their payload capacity can be moderate. Limitations: They are more mechanically complex, potentially meaning higher cost and maintenance. Also, some hybrids sacrifice a bit of efficiency for the VTOL convenience, so they might not match pure fixed-wing endurance or pure multirotor agility perfectly; they’re a compromise. That said, for many corporate security operations, a VTOL drone presents an attractive all-in-one solution: sufficient endurance to patrol large sites and the ability to hover for detailed inspection. As drone technology advances, more refined VTOL security drones are hitting the market, and they are worth considering for forward-looking programs that need both coverage and station-keeping ability.
In addition to these categories, there are specialized platforms like drone-in-a-box systems. These aren’t a different airframe type per se (they are usually multirotor or VTOL drones), but they are sold as an integrated package that includes a sheltered charging station. The drone can land in its “box” which then charges it and protects it from weather, enabling fully automated 24/7 operation. For example, a warehouse might place a drone-in-a-box at the facility’s roof; the drone can auto-launch on a schedule or when triggered by an alarm, then return to recharge – all without human handling. These systems are increasingly popular for corporate security because they minimize the need for on-site drone pilots for routine patrols. The box often has climate control to extend battery life and health. Companies like Percepto and Azur Drones offer such solutions, and even some mainstream drone makers are adding docking stations to their lineup. While these systems involve a higher upfront cost, they effectively turn drones into autonomous security guards that can respond day or night, which might be invaluable for high-security or remote sites.
When selecting a platform, security managers should consider the layout and size of the area to secure, the typical mission profiles (persistent overwatch vs. quick response vs. long patrols), and the available infrastructure for drone operations. Often, the answer might be a mix: multirotors for rapid response and detailed inspection, and perhaps a fixed-wing or hybrid for long-haul surveillance or backup. Compatibility and integration across platforms are also a factor – it may be convenient to stick with a single vendor ecosystem for ease of training and maintenance.
Payloads and Sensors: The Drone’s Toolkit
A drone is only as useful as the sensors and tools it carries. In corporate security applications, the payload – typically a suite of cameras and other sensors – is what allows the drone to detect, recognize, and sometimes deter threats. Here we explore the most common and valuable payload types for security drones:
- High-Definition Cameras (Electro-Optical Day Cameras): The staple of drone surveillance is a stabilized HD camera that provides live video feed and recordings in the visible light spectrum. Modern security drones often feature 4K resolution cameras with high zoom capabilities (20× optical zoom or more is common). This allows operators to get clear details – for example, reading a license plate or identifying a person’s clothing – from a safe height. Many cameras are mounted on a gimbal, giving 360-degree rotation and tilt, so the drone can look in any direction without needing to reposition the whole aircraft. This is crucial for tracking moving targets or scanning wide areas. Some drones even have multiple optical cameras for wide-angle overview and zoomed-in detail simultaneously. In daytime and well-lit conditions, HD cameras are the primary eyes of the drone, capturing color video evidence. They are also useful for documentation (like recording an intruder’s actions for later prosecution, or surveying damage after an incident).
- Thermal Infrared Cameras: Thermal imagers detect heat signatures and form an image based on temperature differences. This is incredibly useful for night surveillance or any low-light environment – where traditional cameras might struggle or require flood lights, thermal cameras can spot humans or vehicles by their heat alone. For security use, thermal payloads allow detection of people hiding in bushes or shadowy areas, and can even help in smoke or fog where visibility is otherwise poor. Many security breaches happen at night, and a person’s body heat is a giveaway even if they wear dark clothing and avoid visible light. Drones equipped with dual optical/thermal cameras give operators a fused view: the thermal image highlights warm bodies, while the optical can often provide identifying details if some light is present. Thermal cameras come in various resolutions (common ones are 320×240 or 640×480 pixel sensors, which are much lower than visual cameras but sufficient to detect humans). When shopping for a security drone, a dual-sensor gimbal (optical + thermal) is highly recommended for 24/7 capability. It effectively turns night into day for the security team. As a bonus, thermal drones can also detect heat anomalies on equipment (like an overheating transformer or a smoldering fire) as part of safety monitoring.
- Low-Light/IR-Enhanced Cameras: Between normal daytime cameras and full thermal, there are cameras specifically designed for low-light conditions. These might include starlight sensors that can capture color video in very dim conditions, or cameras that switch to a black-and-white high sensitivity mode at night. Some drones carry an infrared illuminator (essentially an IR flashlight) and an IR-sensitive camera; this combination works like night vision, illuminating the area with infrared light invisible to the naked eye but allowing the camera to see clearly. This is useful if you want to identify someone at night without using a visible spotlight that tips them off – the drone can quietly light them up in IR and see details. Low-light cameras are not as universally effective as thermal for detection, but they provide clearer facial or object details in darkness when close enough, complementing thermal detection.
- LiDAR and 3D Mapping Sensors: Light Detection and Ranging (LiDAR) sensors use lasers to create precise 3D maps of the environment. In security, LiDAR is less common than optical/thermal cameras, but it has niche uses. One use is intrusion detection: a drone equipped with LiDAR could scan an area and detect changes or moving objects with great accuracy, even distinguishing something small like a crawling intruder in tall grass. LiDAR can also help navigate in GPS-denied environments, although that’s more relevant for autonomy than surveillance. Some high-end security drones might incorporate a LiDAR to map the facility’s layout – useful for creating digital twins of your site or for coordinating autonomous patrol routes with obstacle avoidance. While not a must-have for every program, LiDAR is an example of how drones can carry advanced sensors that turn them into flying inspection tools, beyond just cameras.
- Acoustic Sensors: A newer frontier is putting microphones or acoustic triangulation sensors on drones, to detect gunshots or unusual noises. For instance, a drone could be equipped with a gunshot detection system that alerts when a firearm is discharged, flying immediately to the source. Acoustic sensors on drones face challenges (propeller noise, wind noise), but research is ongoing. Some security scenarios, such as campus security, might benefit from a drone that can “hear” alarms or distress shouts in addition to seeing.
- Deterrence and Response Payloads: Drones can do more than watch – they can act. A range of deterrent payloads are available:
- Spotlights: A high-powered LED spotlight can be mounted to light up suspects on the ground. This has a psychological effect (suddenly being in a drone’s spotlight can freeze a trespasser) and aids video capture. It also helps any responding guards by illuminating the area.
- Loudspeakers: Drones can carry a speaker to broadcast messages or siren sounds. An operator could remotely shout a warning like, “You in the black jacket, you are trespassing – security is en route,” which might prompt an intruder to flee immediately. Loudspeakers are also useful in emergency scenarios to relay instructions to people over a wide area (e.g., in an evacuation, a drone could guide people out).
- Sirens/Strobes: Some drones have built-in loud sirens or flashing strobe lights purely to startle and draw attention. These can be triggered to let an intruder know they’ve been detected and to alert any nearby personnel.
- Delivery Mechanisms: In specialized cases, drones might carry small payload drop systems or attachments (for example, a drone could drop a smoke canister or a GPS tracker onto a vehicle). In corporate security, lethal or harmful devices are not used (weaponizing drones is heavily regulated and generally not ethical or legal for private use). But benign payloads could be used – like dropping a life jacket to a person in water (a lifesaving use rather than security, but worth noting how versatile drones can be). Some security drones also carry non-lethal defense mechanisms; one Israeli firm developed a drone that can deploy pepper spray or tear gas for riot control – however, such uses would require extreme caution and likely law enforcement partnership.
- “Net Guns” or Counter-intruder tech: On the horizon are drones that can intercept other drones (in case an adversary uses a drone against your facility). These often use net launchers. This falls more under counter-drone than routine security, but it’s notable that drones can both be a surveillance asset and also be configured to counter airborne threats if needed (see Future section for more on counter-drone).
When choosing payloads, consider the primary objectives of your drone operations. For most corporate security programs, a combination of a high-resolution day camera and a thermal night camera (often in one gimbal unit) is the baseline. This ensures 24-hour detection and recognition capability. Add a spotlight and loudspeaker if deterrence is part of your plan to intervene on incidents in progress. Ensure the drone’s gimbal can stabilize the camera in wind and during drone motion – clarity of footage is paramount for identifying suspects or situations.
It’s also important to note payload weight and power impact performance. A drone carrying a heavy camera and spotlight will have shorter flight times than one carrying just a small camera. Always check the drone’s specifications for how different payload configurations affect endurance and handling. Many enterprise drones advertise flight time “up to X minutes” which might be with no payload; in real security use with dual cameras and accessories, the flight time could be somewhat less. Plan conservatively in that regard.
From a maintenance perspective, payloads may need their own upkeep – camera lenses cleaned, firmware updated, calibrations done for sensors like thermal imagers. Security managers should include the payload in their maintenance checklists (for example, ensure the thermal camera is properly calibrated for temperature readings if being used to detect equipment overheating, etc.).
Finally, consider future expansion: you might not need LiDAR or advanced sensors now, but choosing a drone platform that supports payload swapping or upgrades can be wise. Some drone systems are modular – you can attach different payloads as needed. This means you could, for instance, use a high-zoom camera during normal operations, but swap in a specialized hazmat detection sensor (yes, those exist – like sniffers for chemical leaks) during a specific incident. While swapping payloads often requires landing and some manual work, the flexibility can greatly increase the drone’s utility across various scenarios, providing a better return on the investment.
Performance Factors: Flight Time, Range, and Weather Resilience
When deploying drones for security, understanding their performance envelope is critical to planning operations. Key performance factors include flight time (endurance), range, speed, maneuverability, and environmental resilience. Here’s what security teams need to know about each:
- Flight Time (Endurance): This is the duration a drone can stay airborne on a single battery charge or tank of fuel. As noted, multirotors generally have shorter flight times (20–40 minutes) while fixed-wings and hybrids can go longer (60+ minutes). Endurance directly affects how you schedule drone patrols. For example, if you need to surveil a perimeter continuously overnight, a single multirotor won’t suffice – you’d need multiple drones cycling in and out of a charging station, or a tethered solution. Many corporate security operations find that having at least two or three batteries per drone is essential: one in use, one charging, one cooled down ready to swap (since batteries heat up and often need to cool before recharging). Advanced drone-in-a-box systems mitigate this by automated battery swapping or charging. It’s also worth noting that real-world flight time can differ from spec sheets: flying in wind, carrying heavier payloads, or lots of aggressive maneuvering will drain batteries faster. Cold weather can also reduce battery efficiency. Security managers should conduct their own tests under typical conditions to know the reliable flight time. As a rule, plan missions to use only ~80% of a battery to leave a safety margin for return-to-base. If a drone has 30-minute average endurance, plan ~20–24 minute patrols then return to swap. Fortunately, battery technology is improving incrementally year by year, and options like hydrogen fuel cells are emerging for longer electric flight. Some security drones advertise swappable battery packs that can be changed in under 2 minutes, minimizing downtime. Endurance is a crucial performance metric because it dictates coverage: a drone with longer flight time can simply do more on each sortie, reducing the number of drones or sorties needed.
- Range and Communication: Range has two aspects – how far the drone can physically fly (which is limited by battery and airspace regulations) and how far the control/data link can operate. FAA regulations (in the US) currently require drones to be within the pilot’s visual line of sight (VLOS) unless you have a special waiver (we’ll cover regulations later). In practice, many enterprise drones use radio controllers that can reach several kilometers. But on a corporate campus, range might be less of a constraint than line-of-sight and signal penetration. If your security office is in the middle of a building, thick walls could reduce control signal range. Many companies use extender antennas or mesh networks so that the drone can stay connected even at the far end of the property. Some advanced systems use cellular (4G/5G) connectivity, allowing a drone to be controlled over virtually unlimited range via the internet – but this may introduce latency and relies on cellular coverage. For most, a range of 1–2 miles is more than enough. It’s important to ensure video feed reliability at range; high-definition video can be bandwidth-heavy, so modern drones use adaptive streaming to keep a stable feed. Executives should know that even if a drone can physically fly 5 miles away, legal and practical considerations usually keep operations much closer (within say 0.5 mile radius for standard VLOS operations). Range can come into play if you have multiple facilities and want to centralize control – e.g., one control center managing drones at two sites a mile apart – which could be feasible with high-range systems or networked control. Ultimately, for corporate security, consistent coverage of your property is the aim, and range specs should comfortably exceed the furthest point you need to reach on your property (with line-of-sight maintained either by the pilot or observers).
- Speed and Agility: Security incidents often unfold quickly, so a drone’s speed can be a factor in how fast it can get on-site. Most multirotor drones fly at around 30–50 mph at top speed. This is sufficient for typical facilities; even a large campus a mile across can be traversed in a couple of minutes at those speeds. Fixed-wing drones, as mentioned, can be faster (60–100 mph), but the trade-off is they can’t stop quickly or hover. Multirotors can dart up and down, pivot in place, and even fly indoors (with proper stabilization sensors). Agility matters if you have a complex environment – lots of buildings, narrow alleyways, indoor-outdoor transitions (some drones can fly inside warehouses to check things then go back out). If you foresee needing to navigate in tight spots (say between refinery tanks or under structures), smaller and highly maneuverable drones might be favored. On the other hand, if your concern is covering a long perimeter quickly (say a fence around 500 acres), a fixed-wing or fast multirotor might be better to do a quick sweep. Also consider climb rate – how quickly a drone can gain altitude. If you have tall structures, you want a drone that can ascend rapidly to go over a building and check the other side when an alarm triggers there. Most quadcopters climb pretty fast (many >10 feet per second). This usually isn’t a limiting factor unless dealing with very tall installations (e.g., monitoring a skyscraper exterior – a niche case, albeit drones are used for building facade inspections, which is analogous to security in some urban settings).
- Weather Resilience: Real-world security operations face all weather conditions: heat, cold, rain, wind, perhaps snow or dust. Not all drones are equipped to handle inclement weather. Rain is a challenge because most small drones are not fully waterproof – electronics and motors can fail if water penetrates. However, there are ruggedized drones with weather resistance (IP-rated casings). Some industrial drones are IP43 or IP45 rated, meaning they can handle light rain or drizzle. A few high-end models boast IP55 or higher, capable of flying in moderate rain and dust. If your security needs must be met regardless of weather – for instance, critical infrastructure sites that cannot have downtime – you should invest in weatherized drones or protective measures (like only flying in rain if absolutely necessary, or using a protective coating). Wind is another big factor. Many drones can handle winds of 10–20 mph without much issue, using GPS and inertial stabilization to hold position. More powerful multirotors and especially larger units can manage 25+ mph winds, though battery drain increases. Fixed-wing drones generally handle wind better in flight (they slice through wind like airplanes), but takeoff/landing in wind can be tricky. If your facility is in a coastal or open area with frequent strong winds, choose a drone with a high wind tolerance spec (often listed as max sustainable wind speed). Temperature affects battery efficiency: very cold temperatures (<0°C/32°F) can reduce battery performance, sometimes by 15-25%. Drones may have battery warmers or you can keep spares warmed in a vehicle before flight. Very hot temperatures can also stress batteries and electronics – ensure the drone’s operating range covers your climate (e.g., up to 40°C/104°F or higher if in a desert environment). Night operations technically are not a weather issue but an environmental one – ensuring your platform has the necessary lights (for FAA anti-collision requirements) and sensors for dark flying (like altimeters or LiDAR for ground sensing) is important if you plan a lot of night sorties. Many enterprise drones now come with all-weather capability because professional users demand it.
- Reliability and Redundancy: Performance isn’t only about how high or fast, but also how reliably a drone performs its mission. Enterprise drones often include redundant components – dual GPS receivers, backup power systems to safely land if the main battery fails, collision avoidance sensors to prevent crashes, and self-diagnostic systems. For example, DJI’s professional drones have multiple IMUs (inertial measurement units) and compasses; if one fails or gives odd readings, the other takes over to keep flight stable. Some even have parachute systems as a fail-safe. When evaluating drones, see if the model has any fault-tolerance features – these add to operational safety which is paramount in corporate environments (you do not want a drone falling out of the sky onto a person or facility asset). Even though such failures are rare, planning for them is part of responsible program management. Regular maintenance (covered next) also ties into ensuring reliability; a well-maintained drone is less likely to have in-flight issues.
Maintenance and Operational Considerations for Security Teams
Deploying drones is not a one-and-done purchase; it introduces ongoing operational responsibilities. Security Directors and Operations Managers need to plan for the maintenance and day-to-day management of the drone fleet to ensure consistent performance and safety. Here are key considerations:
- Routine Maintenance: Just like any vehicle or piece of equipment, drones require regular check-ups. This includes:
- Pre-flight and Post-flight Inspections: Every flight should be preceded by a brief check of the drone’s airframe (no cracks or loose parts), propellers (no chips or warping), battery level and health, sensor functionality, and firmware status. After flight, especially after longer missions, inspect for any debris or wear (e.g., propellers may accumulate bug strikes or dust, which should be cleaned).
- Battery Care: Batteries are a critical component. They should be kept in recommended temperature ranges, not stored fully charged for long periods (most manufacturers suggest storing LiPo batteries at ~50% charge if not used for more than a few days), and cycled (used and recharged) regularly to maintain health. It’s wise to track battery cycles – many smart batteries do this internally – and replace batteries after a certain number of cycles or if capacity significantly degrades. Some companies adopt a practice of labeling batteries and rotating them to ensure even usage. Also, periodic calibration of battery gauges and firmware updates for smart batteries can ensure accurate readings.
- Propeller Replacement: Props can develop micro-fractures or deform over time, which might not be visible but can affect performance. It’s often recommended to replace propellers after a set amount of flight hours or if any incident occurred (like a minor collision or hard landing). They are relatively inexpensive, so erring on the side of caution is fine. Always keep spare propellers on hand.
- Motor and Gimbal Servicing: Brushless motors in drones are robust, but dirt or moisture ingress can cause issues. Listen for any odd sounds (grinding, clicking) which might indicate a motor needs cleaning or replacement. Gimbal assemblies (that stabilize cameras) have delicate parts; ensure they remain responsive and calibrated. Most systems have calibration procedures (either automatic or manual via software) – do this if you see horizon tilt in videos or jitter. Some organizations schedule professional servicing of drones annually or biannually, where the unit is sent to the manufacturer or an authorized shop for a thorough check. This can extend the life of the drone and catch issues early.
- Firmware Updates: Manufacturers periodically release firmware updates that improve stability, add features, or patch bugs (even security vulnerabilities). Assign someone to monitor these releases and apply updates during planned downtime. However, don’t update right before a critical operation – test the new firmware first, as occasionally updates can change behaviors or settings unexpectedly. Keep not just the drone updated, but also controllers, batteries, and any software in the ecosystem (like the base station or tablet app).
- Operational Readiness: Drones should be kept in a state of readiness so that they can be deployed at a moment’s notice for security incidents.
- Charging Regimen: Maintain a rotation such that a fully charged battery is always available for each drone. If using drone-in-a-box stations, they often manage charging automatically (keeping the drone charged and ready). For manual operations, some teams use multi-battery charging hubs. A best practice is to charge batteries after use but not leave them sitting full for too long (to avoid capacity loss) – smart charging cabinets that keep batteries at optimal charge until needed are an emerging solution. One can also implement a daily or weekly routine: for instance, every evening ensure all batteries are at least at 80%, so overnight incidents can be handled; top them to 100% in the morning if a daytime intensive operation is expected.
- Storage and Transport: If drones need to be moved between sites or deployed from a vehicle, invest in sturdy cases. Drones and their equipment should be protected from dust and shock when not in use. A cracked camera lens because a drone slid off a table is an avoidable operational hiccup. Having a proper storage area or charging room at the facility is beneficial – somewhere secure (to prevent theft of the drone itself), climate-controlled, and organized with all the gear.
- Documentation and Logs: It’s important to log flights and maintenance for both compliance and performance tracking. Note flight dates/times, pilot, purpose, and any anomalies or incidents (like if the drone had a GPS signal loss or required a sudden return). Also log battery cycles, replacements, and repairs done. These records help in scheduling maintenance and can be vital in investigating any security or safety incidents (for example, if there were ever a crash, you have records to show proper maintenance and pilot training, which could be important for insurance or regulatory scrutiny).
- Training and Proficiency: A well-maintained drone is only as good as its operator. Ensuring your security staff or dedicated drone pilots are well-trained is an operational must. This includes:
- Initial Certification: In the U.S., any commercial use of drones (which includes corporate security) requires FAA Part 107 certified remote pilots. Ensure all operators obtain this certification (FAA Drone Regulations for Commercial Drone Use: Guide to New Drone Laws and Part 107 FAA Drone Rules | DARTdrones UAV Pilot Training). The training for Part 107 covers airspace rules, weather, drone regulations, and safety – essential knowledge for safe operations.
- Regular Practice: Pilots should fly regularly to maintain their skills. Just like a perishable skill, if a security officer doesn’t use the drone for months and then needs to respond under pressure, their handling may be rusty. Building drone flights into the routine (daily or weekly patrols, even if just for practice or minor tasks) keeps pilots sharp. It also allows them to practice advanced maneuvers or response scenarios so that when a real event happens, they’re ready.
- Scenario Drills: Incorporate drones into security drills. For instance, run a simulation of an intruder breaching the fence: have the drone team respond as they would in reality, coordinate with ground security, track the “intruder,” and see how well information is communicated. These drills will help iron out protocols (e.g., how the drone pilot hands off info to the guard team, what the guard does if the drone loses sight, etc.). It will also boost confidence in the system’s effectiveness or highlight areas for improvement.
- Cross-Training: It might be wise to cross-train multiple personnel on basic drone operation, even if only one or two are primary pilots. In an emergency, you don’t want capability limited to a single person. Operations managers can ensure at least all shift supervisors know how to launch a drone and take over in an emergency if the primary pilot is unavailable.
- Integration with Security Team Workflow: Drones should become a seamless part of the security ecosystem, not a standalone novelty. Operationally, this means:
- Establish clear SOPs (Standard Operating Procedures) for when and how drones are to be used. For example, “If perimeter alarm triggers and drone is available, deploy drone before sending patrol officer, unless human response is immediately required for safety.” Or “Drone shall conduct a full perimeter sweep at the start of each shift and report any irregularities.” By formalizing these, you ensure consistent usage and maximum benefit. (We will talk more about developing SOPs in the implementation section, but from a tech perspective, your SOPs will also cover maintenance tasks like pre-flight checklists and fail-safe procedures).
- Communication protocols: How does the drone operator communicate with other security team members? Typically via radio – ensure the pilot has access to the security radio channel or a dedicated line to the SOC (Security Operations Center). The pilot might also need to communicate with external entities (like local law enforcement or, in some cases, air traffic control if operating near airports with prior approval). Having pre-established contacts and scripts for those communications is valuable. For example, if the facility is near an airport and you have an agreement to notify the tower when the drone is airborne, that should be in the checklist.
- Data management: Operationally, decide what happens to the video footage and data the drones collect. Is someone monitoring live video at all times (perhaps in the SOC)? Are recordings stored, and for how long? A common practice is to treat drone video like CCTV video – recorded and retained for X days unless needed for an investigation. Ensure you have the storage infrastructure if you plan to keep high-resolution recordings (it can accumulate quickly – hours of 4K video take a lot of disk space). There are video management systems (VMS) that can ingest drone feeds along with fixed cameras; integrating into those may streamline data handling. Also consider if the data needs to be encrypted or access-controlled to prevent unauthorized viewing – drones could capture sensitive views (like into private areas), so only authorized staff should be able to access the feeds and archives.
- Contingency Planning: Murphy’s law applies – batteries die, weather turns foul, or a drone might have a fault at a critical time. Operational planning means having backup measures:
- If Drone A is down for maintenance, do you have Drone B ready? Many programs start with at least two drones for redundancy.
- If weather prevents flying (e.g., thunderstorm), ensure traditional security measures are ready to fill the gap (maybe schedule an extra guard patrol in heavy fog since drones can’t fly safely).
- If a drone malfunctions mid-mission, have a procedure: Most drones have an auto “Return-to-Home” on low battery or loss of signal – configure that home point properly (usually the launch point or a safe landing area) and train pilots on using emergency modes. If a drone is about to crash or drift, do they know how to safely cut power or regain control? This comes from training but should be emphasized in SOPs.
- Also, consider insurance and liability: As part of operations, ensure your company insurance covers drone operations (often it can be added as a rider or separate policy for aviation liability). Have a plan for incident response if a drone accident occurs (e.g., secure the area, recover pieces, report to the FAA if required – serious accidents must be reported per Part 107 rules).
- Lifecycle and Upgrades: Operational planning includes the lifecycle of equipment. Drones are tech gadgets at heart and can become obsolete or less effective as new models with better features come out. A wise approach is to budget for periodic upgrades or expansions. For instance, plan that drone airframes might be replaced or significantly upgraded every 3-5 years to keep up with improvements (like longer battery life or better sensors). This prevents being caught off-guard when manufacturer support ends or when your drones no longer meet the demands (maybe you need more advanced detection that new drones provide). Keeping an eye on industry developments (which we cover in the Future section) will help plan these upgrades. It’s also a reason to maintain good relationships with vendors or integrators – they can alert you to useful upgrades or trade-in programs.
- Security of the Drones (Cyber and Physical): This is sometimes overlooked: drones themselves are part of your security infrastructure and must be secured. Physically, store them in a locked area to prevent tampering or theft. Digitally, protect the control systems – use encrypted links if available, change default passwords on any software, and ensure that data links have encryption (many enterprise drones do). Be mindful that some drones, especially those connected to cloud services, might upload data – ensure compliance with your company’s cyber policies and consider network segmentation for drone controllers. Also, Remote ID (a new FAA requirement) means your drones will broadcast an ID that law enforcement can pick up; ensure you’ve complied and registered those as needed (more in regulations section). While not an operational “maintenance” in the traditional sense, cyber maintenance (keeping software updated, following best IT practices) is part of drone operations now.
In conclusion, maintaining drone technology in a corporate security setting requires procedural discipline and integration with existing security operations. The hardware is sophisticated but needs care; the team is capable but needs training and practice. With solid maintenance schedules, trained personnel, and integrated protocols, drones can be a reliable and effective part of the security apparatus, running like a well-oiled machine (or rather, a well-charged device). It’s often useful for Security Directors to create a maintenance and operations manual specific to their drone program, incorporating manufacturer guidance and their own SOPs – essentially, a handbook that ensures continuity even if staff changes. By treating drones with the same rigor as one would treat, say, a company fleet of vehicles or an important IT system, you ensure they’ll be ready to deliver critical surveillance intelligence whenever and wherever needed.
Core Applications & Sector-Specific Use Cases
Having explored the technology, we now turn to practical applications – what exactly can drones do in the field of corporate security, and how are they being used across different industries and scenarios? In this section, we detail the core use cases for drone surveillance, from routine perimeter patrols to rapid incident response. We’ll also present anonymized or hypothetical case studies that illustrate these use cases in action, demonstrating the tangible benefits achieved. Different sectors – such as logistics, critical infrastructure, retail, and campus environments – have unique security challenges; we will examine how drone solutions can be tailored to each. The goal is to translate capabilities into real-world operations and show Operations Managers how to deploy drones for maximum impact in their specific context. (Where possible, we’ll also note any lessons learned or operational insights that can help ensure these deployments run smoothly.)
Perimeter Patrol and Intrusion Detection
One of the most popular applications of security drones is perimeter surveillance. Virtually every facility – from warehouses and factories to corporate office parks – has a boundary that needs monitoring. Traditionally this might be done with fence sensors or periodic guard tours. Drones revolutionize perimeter security by providing frequent, mobile patrols that can cover the entire boundary quickly and detect anomalies in real time.
Use Case Example – “Eagle-Eye Perimeter Watch”: Consider a large distribution center of about 200 acres, surrounded by a chain-link fence. The site experienced occasional night-time fence breaches where thieves cut the fence to steal stored goods. The security team deployed a drone with an optical/thermal camera to fly along the fence line every hour at night. The drone’s thermal imaging could see if anyone was lurking outside the fence or if a section of fence was disturbed (the temperature difference of a fresh cut or a person’s handprints on metal can sometimes be seen). On one occasion, the drone’s operator noticed an unusual heat spot near the fence in a remote corner – zooming in, they saw two individuals hiding by the fence where they had just cut an opening. The operator immediately triggered the drone’s spotlight and loudspeaker, announcing that security forces were on their way. The suspects, startled and aware they’d been spotted, fled before stealing anything. Ground guards were dispatched to that fence segment and secured the cut. Result: an attempted theft was deterred without any loss, and repairs were made before dawn. Over several months, the mere knowledge that a drone patrols the fence regularly (signs were posted noting “Drone Surveillance in Use”) dramatically reduced fence-cut attempts. The ROI was clear as inventory losses dropped to near zero.
From this example, we see key benefits: early detection, deterrence, and rapid coverage. A drone can typically fly the entire perimeter of a facility in minutes. Modern drones can even do this autonomously on a programmed path, using GPS waypoints or following the fence line via machine vision. If integrated with intrusion sensors, the drone might not even have to patrol constantly – it could be automatically dispatched the moment a fence sensor triggers, potentially catching intruders in the act. Compared to a walking patrol that might take an hour to circuit the property (and might pass a given point right before intruders strike there), a drone can be on the scene far more responsively and persistently hover to monitor until backup arrives.
For critical infrastructure sites like power plants or data centers, perimeter drone patrols add a high level of assurance. Some companies use drones with thermal cameras specifically to spot anyone approaching the perimeter in darkness, because the thermal signature pops out against a cooler background (Navigating Modern Security Challenges: The Crucial Role of Physical and Surveillance Security Solutions – Cuneo Consulting). Drones can also cover perimeters that are hard to access on foot – for example, a facility with a waterfront boundary (drones can fly over water) or rugged terrain. If a site has an external perimeter and an internal one (say a secondary fence or building line), the drone can check both in one flight by doing concentric loops.
Operational insight: When using drones for routine patrols, vary the schedule or pattern if possible. Predictable patterns could theoretically be timed by savvy intruders. Drones give the ability to be unpredictable – use that advantage (e.g., sometimes do two back-to-back patrols, sometimes skip an hour, etc.) to keep adversaries guessing.
Asset Protection and Asset Tracking
Beyond just the perimeter, drones are very useful for watching over specific high-value assets or areas within a facility. This could mean monitoring an outdoor yard with expensive equipment, tracking the movement of sensitive materials, or keeping an eye on a remote warehouse on a property.
Use Case Example – “Overwatch for the Loading Yard”: A large manufacturing company has a secured yard where finished products on pallets are staged before shipping. These products are high-value, and there were incidents of tampering and theft in the past. The yard is too large to cover with static cameras everywhere (and moving goods sometimes block views). The company introduced a drone surveillance routine focused on this yard. Whenever a shipment is being prepared or moved, a drone takes off and hovers above the yard, providing a live overhead feed to the security operations center. This aerial perspective allows security to track the assets (pallets, containers, etc.) as they are moved by forklifts from storage to trucks. If any unauthorized activity occurs – e.g., a pallet being moved to an unusual location – the security team sees it immediately. In one scenario, the drone feed helped catch an operational issue: a driver attempted to leave with a truck before proper sign-off, which could have been theft or simply a mistake. The drone noticed the truck departing the loading bay without clearance and alerted security to stop it at the exit gate. It turned out to be a miscommunication, but it illustrated how constant eyes on assets prevent things from slipping through cracks. The workers in the yard also knew they were being observed, which improved compliance with protocols (like no leaving pallets unattended). Result: No more losses occurred from the yard, and inventory accountability improved. The overhead footage also proved useful for operational analysis – the logistics managers reviewed it to optimize the layout and flow of the yard.
This example shows drones acting as a roving CCTV, but with the flexibility to follow assets around. For companies with large outdoor storage (construction materials, vehicles, etc.), drones can do regular inventory sweeps, literally flying grid patterns over a laydown area to check that everything is in place. With machine learning, some systems can even automate counting or recognizing objects (for instance, matching what’s supposed to be there versus what the drone sees).
In sectors like logistics and trucking, one use case is to have a drone automatically track high-value shipments. Imagine a scenario: a truck carrying valuable microchips enters a big industrial campus. A drone could follow that truck from the gate to the loading dock, keeping an eye on it to ensure it isn’t intercepted or tampered with on the way. This might sound extreme, but in some environments (say large ports or multi-tenant industrial parks), it adds a layer of security for critical deliveries.
Another asset-related use is protecting company vehicles or machinery. For example, mining or energy companies with lots of equipment might use drones at night to ensure expensive machinery is not being disturbed. Drones can also check on remote assets like pipeline valves, solar panels, or telecom towers in a corporate network, blending security and maintenance inspection.
The key insight for asset protection is that drones provide on-demand visibility exactly where you need it, when you need it. They can bridge gaps between static cameras or go to places that are cost-prohibitive to wire with CCTV (like acres of materials or an open field parking lot). By actively tracking asset movement, they reduce reliance on after-the-fact audits – you have a real-time audit as things move.
Rapid Incident Response and Emergency Support
When an alarm goes off or an emergency happens on site, every second counts. Drones shine in incident response by being first on scene to assess and sometimes even intervene. We touched on this in earlier sections as a strength; here, let’s focus on specific scenarios and sector angles:
Use Case Example – “Eyes on the Alarm”: A research campus has multiple buildings with sensitive laboratories. In the middle of the night, a motion detector alarm triggers in one lab building. The standard procedure would be to dispatch the on-call security patrol driving from the central office, which could take 5–10 minutes across campus. Instead, their new SOP sends a drone immediately. The drone, resting in its charging dock on the roof of the security office, launches within a minute of the alarm. It zips to the coordinates of the alarm (they have preset GPS points for building entries) and arrives outside the lab building in about 90 seconds. Using its camera, the operator guides it to hover near a window of the lab. Peering through, the infrared view shows no obvious person or movement – but it does show a heat plume near a piece of equipment. Switching to the optical camera, the operator sees that a small fire has started on a lab bench (perhaps the cause of the alarm). Immediately, they relay this to emergency services. The drone hovers at a safe distance but continues to give a view of the room until firefighters arrive, allowing security to inform them if the fire is spreading or if anyone is inside (no people were visible, thankfully). By the time the first responders and security personnel reach the lab (a few minutes later), they are aware of exactly what they’re dealing with, and they quickly extinguish the small fire. Outcome: The quick eyes-on by the drone confirmed it wasn’t an intruder but a fire, enabling the appropriate response and minimizing damage.
In this case, the drone cut through the ambiguity of an alarm – whether it was a break-in or accident – and sped up the critical information flow. This application is universally valuable: situational awareness. In emergencies like fires, chemical spills, or medical emergencies on a large campus, a drone can often arrive before ground staff, providing a live feed that can be shared with responding teams. Some companies have integrated drones into their emergency response plans, where security drones work alongside safety officers. For instance, if a fire alarm goes off in a chemical plant, a drone might be tasked to check the storage tanks area to ensure no secondary issues, while humans focus on evacuation.
For security incidents specifically (like intrusions, active threats), drones can be a game-changer. One particularly compelling scenario is an active shooter or armed intruder on a campus. Sending unarmed security or even police blindly into such a scenario is dangerous. A drone could be sent into the area (even indoors, some companies have drones that can autonomously navigate hallways) to locate the suspect and track them from a safe distance (Drone as a Security Service: Is It Right for Your Business?) (Drone as a Security Service: Is It Right for Your Business?). Live video to law enforcement can help them plan an approach or even communicate with the suspect via the drone’s speaker. This is a very specific and high-stakes use, but worth noting how drones add a layer of safety.
In more everyday terms, alarm verification is hugely useful. Many corporate security operations deal with frequent false alarms (motion sensors triggered by HVAC drafts, wildlife tripping outdoor sensors, etc.). Drones enable a “trust but verify” approach: you don’t ignore alarms, but you also don’t have to send a whole team out every time at great cost. The drone does the recon. Over time, this can save labor and reduce disruption, since genuine alarms get priority response and false alarms get a quick check with minimal fuss.
Also, consider integration with access control: If a door forced-open alarm triggers in a building, that might indicate a break-in. A drone can be dispatched to that door’s location and peek at it – if a door is ajar and no one’s around, maybe someone pried it then ran; the drone can then sweep inside if safe or track any suspect leaving. If the door is closed and no visible issue, it might have been a sensor glitch and a less urgent response is fine.
Cross-sector examples:
- Manufacturing/Industrial: Drones respond to machinery alarms or hazardous material alarms, giving visual confirmation if there’s a leak or if it’s a sensor error.
- Airports or large campuses: Drones are sent to far-flung perimeter breaches (like a hole in a fence on the far side of an airfield) – they can get there faster than a patrol vehicle that has to drive around runways.
- Public events at corporate venues: If a company is hosting an event (concert, fair) and an incident (like a fight or medical emergency) is reported in the crowd, a drone can be overhead to coordinate crowd management and guide responders (security can see best route through the crowd via drone’s view).
One should note, however, privacy and safety considerations especially for incident response involving people – which we’ll cover under ethical considerations – but operationally: don’t fly drones in a way that endangers responders or bystanders. In emergency support, altitude and stable hover are your friends (stay out of the way, but watch).
Sector Spotlight: Logistics and Warehousing
Sector Context: Warehouses, distribution centers, and logistics hubs typically have vast indoor and outdoor areas, heavy vehicle movement, and valuable stock. Security challenges include theft (internal or external), trailer and cargo tampering, perimeter breaches, and ensuring safety protocols are followed (like no unauthorized persons in loading zones).
Drone Applications in Logistics:
- Yard Management: As mentioned, overseeing loading docks and trailer yards is a big use. Drones can also read container or trailer numbers with high-res cameras, helping keep track of assets in large truck lots. This can complement RFID-based systems – if a tag is missed, a drone scanning might catch a trailer that isn’t where it’s supposed to be.
- Intrusion Watch: Large warehouses are often targets for break-ins. Drones can continuously orbit the facility exterior at night, covering blind sides not visible from the guard shack. Some logistics companies also use drones to check roof accesses (thieves have been known to cut through roofs to enter warehouses). A drone can land or hover above the roof to inspect for any fresh cut or movement.
- Indoor Patrols: A cutting-edge practice in big warehouses (especially high-value goods like electronics) is using small indoor drones to do aisle inspections after hours. These drones fly autonomously using QR codes on the ceiling or other navigation guides, scanning inventory and checking no one is hiding inside after closing. They can also check for safety issues (like no smoldering fire or electrical problem). Companies like Verity have drone systems for automated inventory counts – which is dual-purpose for security because if inventory is missing or moved, that’s a security concern too.
- Worker Safety and Compliance: Drones can monitor if forklifts are operating safely, if safety vests are being worn, etc. While this veers into operations management, it’s all part of overall security and risk management for logistics sites.
Hypothetical Case: A retail distribution center had a recurring issue of missing merchandise. They suspected some employees were stashing goods in remote corners of the warehouse to retrieve after hours (a form of pilferage). Installing cameras in every single aisle was impractical. Instead, they began random drone fly-throughs inside the warehouse during breaks and after shifts, with the drone’s camera scanning shelves and looking for any unusual boxes left out of place. One evening, the drone spotted a pile of high-end electronics hidden behind some pallets at the back of a rack – a clear sign of attempted theft. Security then set a trap, surveilling that spot and catching an employee in the act of trying to remove it after hours. After a couple such interventions (and word getting around), the pilferage stopped. The drones essentially acted as random inspectors that could appear anywhere, enhancing overall security inside the vast facility.
Sector Spotlight: Critical Infrastructure (Energy, Utilities)
Sector Context: Critical infrastructure sites like power plants, substations, oil & gas facilities, telecom installations, and transportation infrastructure face not just theft, but also sabotage and safety risks. They often span large outdoor areas, sometimes in remote locations. Security is paramount due to the potential impact of incidents (e.g., a breach at a power substation could cause outages).
Drone Applications in Infrastructure:
- Long Range Patrols: Pipeline companies use drones to fly along pipelines to detect unauthorized activity or tapping. Utility companies fly drones along transmission lines or around substations to look for intrusions or even to inspect fences and equipment (overlapping maintenance).
- Protecting Restricted Zones: Many infrastructure sites have buffer zones. Drones can monitor these perimeters from above, including areas that might be swampy, hilly, or otherwise hard to traverse. For example, a hydroelectric dam might deploy a drone to monitor the reservoir side and downstream side for any suspicious boats or people approaching restricted areas.
- Emergency Response: In power plants, drones can be launched if an alarm indicates a malfunction in one section – they provide visuals for engineers and security to decide if it’s a security issue or an operational failure. In case of a security breach or terrorist attempt, drones give situational awareness that is invaluable for an organized response with law enforcement.
- Night Surveillance: Many critical sites are dark at night for safety or stealth reasons (not to draw attention). Thermal drones come into play heavily here to catch any movement. For instance, in a solar farm at night, a person walking among panels would light up on thermal like a beacon, whereas cameras would see pitch black.
- Case Study Insight: A utility substation in a semi-rural area had repeated vandalism (people shooting at transformers or copper theft attempts). The utility installed motion sensors but response was slow due to distance. Now, a drone stationed at a nearby service center can fly to the substation in about 2 minutes on any alarm. In one incident, the drone arrived while vandals were still on site, captured clear video of them (including faces, as it got fairly close with a zoom lens), and played a loud warning. The vandals fled, but the footage was given to police, leading to their identification and arrest. Since then, the mere knowledge of drones present (signs posted and perhaps local media coverage of the arrest) has deterred further incidents.
Sector Spotlight: Corporate Campuses and Offices
Sector Context: Corporate campuses (like tech company headquarters, office parks, university-like settings) and office high-rises have a mix of open areas, parking lots, and buildings. Threats can range from unauthorized visitors (protesters, spies) to workplace violence or petty crimes like car break-ins. Executives and intellectual property might be targets, raising the stakes for security.
Drone Applications in Campus Security:
- Parking Lot Security: Large campuses with multiple parking lots or garages can use drones to patrol these areas, especially at shift changes or overnight. This both deters car break-ins and can provide escort overwatch for employees walking to their cars late (an operator can direct a drone to hover above an employee and ensure they reach their car safely, a service some employees appreciate).
- Event Monitoring: Companies often host big events (product launches, all-hands meetings, etc.). Drones can supplement security staff by providing crowd observance from above, detecting any disturbances or unauthorized persons quickly. They can also watch perimeter points that might be exploited to sneak in.
- Executive Protection: If high-profile executives are moving around campus (especially outdoor segments between buildings), a discreet drone could keep a distant watch to spot any approaching individuals or drones (for counter-drone) posing a threat. This is a rather specialized use, but not far-fetched for VIP security – think of it as an aerial bodyguard scanning rooftops and far angles that ground bodyguards might miss.
- Building Checks: For offices, drones can inspect rooftops or upper floors externally. There have been cases of activists scaling buildings to put up banners, etc. A drone can quickly check if something odd is on the building facade. It can also look for maintenance issues that could become security hazards (like a broken window on a high floor that someone could exploit to enter).
- Campus Perimeter: Many corporate campuses have an outer boundary that’s porous (roads, landscaping). Drones can loop around these to watch for any trespassers or suspicious parked vehicles surveilling the site.
Hypothetical Campus Scenario: A tech company’s campus has experienced some incidents of unauthorized drones flying over (potential espionage or nuisance) and one case of an intruder who blended with a tour group. In response, the security team uses their own drones not just for surveillance but as part of counter-surveillance. When an unfamiliar drone was spotted in the area, the security drone was launched to investigate (they located an operator in a nearby parking lot, and police were called – turns out it was a hobbyist, but the quick response set a tone that such incursions won’t go unchallenged). In another instance, an employee reported a strange person in an employee-only courtyard; the drone got there fast and tracked the individual as they tried to move toward an exit – guards were guided straight to them and intercepted. It was a former contractor who wasn’t allowed on site. Thus, the campus drones acted as both a detection tool and a coordination tool guiding security through a maze of buildings to exactly where they needed to be.
Sector Spotlight: Retail and Commercial Properties
Sector Context: Large shopping centers or retail complexes, as well as commercial properties like malls or casinos, have public visitors, large parking areas, and valuable inventory or assets (stores). Security concerns include shoplifting, parking lot crime, crowd control, and after-hours break-ins.
Drone Applications in Retail Security:
- Mall Parking Surveillance: Much like campus parking, but perhaps focusing more on deterrence of vehicle break-ins and quick response to incidents like fights or accidents in parking lots. A drone could patrol the mall parking during busy seasons (holiday shopping) when those incidents spike.
- Rooftop & Backdoor Monitoring: Malls and big-box stores often have extensive roof areas where thieves may attempt to break in (cutting through roofs into jewelry stores, for example, has happened). Drones can routinely check rooftops at night for any signs of entry. Also, drones can check service alleyways behind stores where loading docks and back doors are – areas that are otherwise deserted at night and vulnerable.
- Crowd/Event Management: If a new product release causes people to line up outside a store (think new phone release at an electronics store), a drone can help observe the queue for any disorder, allowing the limited security staff to manage large crowds more effectively. Similarly, at open-air shopping events or concerts at a commercial venue, drones augment the security presence.
- Emergency Response in Public Areas: If there’s, say, a lost child in an amusement park or an active threat in a mall, drones can provide overwatch that helps coordinate evacuation or search. Some malls are experimenting with drones as part of their active shooter drills to see how to direct fleeing crowds away from danger by using aerial perspective.
Hypothetical Retail Scenario: A large outlet shopping center implemented a drone unit to fly over the premises on weekend nights when incidents were common. One evening, after closing, the drone detected a heat signature on the roof of a closed department store. Closer inspection revealed two individuals trying to cut a vent grate – clearly burglars attempting a roof entry. The drone operator immediately alerted on-site security and police. The drone kept eyes on the suspects (who didn’t realize they were watched from above in the dark) until officers stealthily surrounded the building and made the arrest. The store manager was amazed – previous attempts at catching these roof thieves (they had hit other stores in the region) had failed, but the aerial thermal vantage made all the difference. Additionally, in daytime, the same drone program had been useful for catching shoplifters who would run through parking lots; by tracking from above, none escaped despite weaving between cars.
Operational Insights for Different Roles
Throughout these use cases, different roles in an organization will care about different aspects:
- Operations Managers: They will focus on how drones can streamline daily security operations and incident handling. For them, key insights are efficiency gains (e.g., one drone operator can cover what might require 3 patrolling guards), and the ability to respond swiftly without overextending personnel. Ops managers should look at scheduling drones in a way that complements guard shifts – perhaps using drones heavily in the late night hours when fewer staff are on site. They should also consider things like noise (drones do buzz; using them when they won’t disturb visitors or employees is wise – or choosing quieter models for when used around people).
- Security Directors: They’ll be looking at the overall risk reduction and how drones fill gaps in the security plan. They’ll want to align use cases with the biggest vulnerabilities identified in risk assessments. For example, if a vulnerability is lack of surveillance in a certain remote corner after dark, that becomes a priority use for the drone. They also need to ensure coordination: that drone operators know what to do when they spot something (how to report it, log it, escalate it).
- IT/Technical Teams: For implementing these use cases, integration is key. If a use case involves automatically dispatching a drone on an alarm, that means integrating the alarm system with the drone control software. IT might need to help with that. Also storing video feeds, ensuring network can stream from drone to control center (especially if using multiple drones at once).
- Compliance and Safety Officers: They will want to ensure none of these operations violate privacy or safety guidelines. For instance, using drones around crowds must be done at a safe altitude to avoid any chance of injury if something fails. Privacy considerations come in if drones are recording people (we will cover more in ethics, but operationally they might restrict certain uses like not zooming in on employees unless a security incident justifies it).
Across sectors and use cases, one general insight emerges: drones extend the reach and capability of the security team, but they work best when integrated with the team’s procedures. The technology is impressive, but it’s the tactics and strategies behind deploying it that actually stop the bad guys or manage the crisis. Every organization should tailor drone use to its site layout, threat profile, and team structure. It might start small – one or two key use cases – then expand as comfort and proficiency grow.
Finally, let’s highlight a short list of Core Takeaways for Use Cases:
- Drones excel at perimeter defense, providing an agile sentry that dramatically cuts response times to fence alarms and deters intrusion.
- They can guard valuable assets in motion or in storage, effectively following the trail of goods to prevent and document theft.
- Drones act as a force multiplier in incidents, being first on scene to feed situational intel to responders, whether it’s a security breach or a safety emergency.
- Sector-specific needs shape deployment: e.g., logistics benefit from yard monitoring, infrastructure from long-range patrols, campuses from flexible coverage of open areas and events.
- Case studies consistently show incidents either prevented or resolved faster thanks to drones – from catching thieves to managing crowds – which reinforces that drone surveillance is not theoretical but delivering real improvements in security outcomes.
With these concrete applications illustrated, organizations can see how drone surveillance moves from an idea to a daily reality on the ground (and in the sky). Next, we will discuss how to integrate drones so that they mesh with other security components, creating a unified system rather than a standalone tool.
Seamless Integration Strategies: Creating a Unified Security Ecosystem
Introducing drones into a corporate security program should not happen in a vacuum. To unlock their full potential, drones must be integrated into the broader security ecosystem – connected with other surveillance systems, communication networks, data platforms, and operational workflows. In this section, we’ll explore how to weave drone operations into a unified security fabric. We’ll cover integration with existing security tech like Video Management Systems (VMS), access control and alarm systems, and discuss how to build centralized command centers that can handle drone feeds alongside other sensors. We’ll also look at data management and analysis: once drones are feeding new streams of video and alerts, how do you store, process, and act on that information effectively? Finally, we provide compatibility guidance and best practices to ensure Security Directors and IT teams can deploy drones that play nicely with their current infrastructure. By achieving seamless integration, drones become an organic extension of your security operations, rather than a standalone gadget.
Integrating Drones with Video Management and Alarm Systems
Most organizations already have some form of electronic security system – CCTV cameras monitored through a VMS, intrusion detection systems that trigger alarms, and so on. For drones to add value, they should augment and interface with these systems, not operate as a separate silo.
Video Management System (VMS) Integration: A VMS is the platform that displays and records feeds from CCTV cameras. Modern VMS platforms (like Genetec Security Center, Milestone XProtect, etc.) increasingly offer the ability to incorporate drone feeds as just another camera view. This means a security operator in the control room could see the drone’s live video on the same video wall as the parking lot cameras and building cameras. The benefit of such integration is operational continuity: operators don’t have to switch apps or screens; they can track suspects from a fixed camera and then seamlessly transfer to the drone’s perspective, for example.
Some specific integration points:
- RTSP/ONVIF Streams: Many drones (or their controller software) can output an RTSP video stream. If configured, the VMS can treat the drone like an ONVIF-compliant camera (Cost-Effective Security: Comparing Drone Security to Traditional Methods) (Cost-Effective Security: Comparing Drone Security to Traditional Methods). For instance, when the drone is in flight, its video appears on a VMS channel (perhaps labeled “Drone 1 Camera”). One can even set it to record automatically whenever the drone is flying, so all footage is stored in the central video archive.
- PTZ Controls: If the drone feed is integrated, some VMS allow you to use the interface to control the drone camera like a PTZ (Pan-Tilt-Zoom) camera. Realistically, controlling a drone fully via VMS is complex, but at least the camera gimbal could respond to commands. More practically, integration means the operator can focus on analyzing what they see rather than juggling tools.
- Auto Pop-up on Alarm: Imagine an alarm triggers and a drone is launched in response; if integrated, the VMS can automatically display the drone feed on the big screen or send it to the guard’s mobile device. This speeds up awareness.
Access Control and Intrusion Alarm Integration: Access control systems manage doors and entrances; intrusion systems handle motion detectors, glass-break sensors, etc. Many have central management software. Integration can occur in a couple of ways:
- Automated Drone Dispatch: A sophisticated integration would involve the alarm software sending a command to the drone control software when certain alarms occur. For example, if a fence sensor (intrusion alarm) goes off at Zone 5, it could trigger a script that tells Drone 1 to take off and go to pre-set GPS coordinates at Zone 5. There are already products and partnerships making this possible; some drones can receive API commands to launch and navigate to a point. If direct integration is difficult, this can be semi-automated: the alarm system could notify the drone pilot’s console with the coordinates so the pilot just approves the launch with one button. The goal is to compress the time from alarm to drone airborne.
- Unified Dashboard: Some security management platforms aim to unify all functions – essentially PSIM (Physical Security Information Management) systems. If you have such a platform, you’d want the drone to be a sensor/actor within it. For instance, a unified system might log: “Motion detected in Warehouse A at 22:14 – Drone 3 dispatched at 22:15 – Drone live feed [link] – Guard patrol alerted at 22:16.” This unified logging and control leads to better incident handling and post-incident analysis.
- Access Control Integration: Not as direct, but a scenario: if someone uses a stolen badge to enter a building, the access system could flag an anomaly (maybe the real badge owner is known to be elsewhere). A drone inside could be alerted to go to that lobby and surveil the person until security intervenes. That’s a complex integration, but conceptually possible (requires advanced identity systems). More immediate is using drones to respond if a door is forced or held open: those events can queue a drone to inspect that doorway area.
Central Command Centers and Unified Interface: For organizations scaling up drone use, it may make sense to have a Drone Operations Center, or fold it into an existing Security Operations Center (SOC). This could be a room where dedicated screens show a map with drone locations, telemetry, etc., next to the usual security displays. Ideally, one unified interface would show:
- A map of the facility with real-time positions of each drone (many drone softwares have maps).
- Icons for other security elements (camera locations, guard locations if using guard tracking, alarm points). This GIS approach to security can let an operator drag and drop a drone icon to an alarm icon and thereby dispatch it, for example. Some vendors offer these integrated command center solutions for critical infrastructure where they integrate fixed sensors, drones, and even ground robots on one screen.
For example, Cuneo Consulting might design a unified command center where drone feeds and data streams are integrated with motion sensor and CCTV analytics into a single dashboard (Navigating Modern Security Challenges: The Crucial Role of Physical and Surveillance Security Solutions – Cuneo Consulting) (Navigating Modern Security Challenges: The Crucial Role of Physical and Surveillance Security Solutions – Cuneo Consulting). The integrated analytics could even suggest actions (e.g., “Intruder detected by AI on Camera 12 – Drone 2 suggested for dispatch”).
From the human perspective, integration means simplifying the job of security personnel. The drone essentially becomes another patrolling guard, whose “bodycam” is visible to dispatch and whose location is known on the guard tracking board. By reducing friction (like not having to pick up a separate controller unless manual flight is needed), you make it more likely that drones will be used consistently and effectively, rather than sitting idle because staff find it too cumbersome.
One challenge is that many corporate security setups use products from different vendors. Integration often requires custom work or middleware. Security directors should insist on open APIs and interoperability when choosing drone systems. There are emerging standards and alliances focusing on unified security ecosystems where drones are just one part. If your current integrator or security software supports certain drone brands more easily, that’s a factor to consider in choosing hardware.
Lastly, training on integrated systems is vital. If operators are used to traditional CCTV monitors, they need to train on the new interfaces that incorporate drones, so they trust and know how to command these new tools fluidly.
Unified Data Management and Analytics
Drones will generate a significant amount of data, primarily video footage, but potentially other sensor data (thermal images, metadata like GPS coordinates, etc.). Properly managing this data ensures it can be used for real-time decision-making and post-event analysis without overwhelming the system or violating policies.
Storage and Retrieval: Consider how long you need to retain drone video. Many corporate policies for CCTV footage retention range from 30 to 90 days, unless flagged for an investigation. Drone footage can be similarly archived. Because drones might record 4K video, storage requirements can grow quickly – but you can mitigate this by recording only when the drone is on a mission, and maybe at 1080p if 4K detail isn’t needed. Ensure your VMS or storage server is configured to handle these additional feeds. Marking drone footage with metadata (date, time, location tags) is helpful for search. For example, after an incident, you might want to quickly retrieve the drone’s video of it – having it labeled by incident ID or alarm ID would be ideal, which implies some integration or at least a careful manual logging process by the operator.
Data Security: With drones collecting sensitive visuals (e.g., around private property or capturing employees), securing that data is critical. Integrated systems should enforce that drone video is stored in the same secure manner as other security footage – encrypted storage, access logs for who views it, etc. Additionally, if using cloud services for video (some drone systems offer cloud video management), compliance with company data policies is needed. Some companies may choose to keep all drone data on-premises to avoid any leaks. This ties into privacy, which we’ll discuss later, but from an IT perspective, treat the drones as new cameras that need the same cybersecurity protections as any IoT device on the network (Do Drone Users Care About Data Security – DRONELIFE) (ensuring the drone’s wireless link is encrypted, that drone control tablets are secure, etc.).
Real-time Analytics: A big integration opportunity is applying AI analytics to drone video feeds similar to how it’s applied to fixed CCTV. For example, many VMS or analytics systems can do object detection (person, vehicle) in video. If you can pipe drone video into that, you could get automatic alerts like “person detected in restricted zone by Drone 1” without the operator noticing manually. This is cutting-edge but feasible; however, it may require high-bandwidth streaming and computing power. Some drones come with onboard AI (like DJI’s newer enterprise drones that can recognize people or cars and track them). If so, integrate that metadata – e.g., the drone itself might flag “human detected” and that alert could be sent to the security center even if the video isn’t being actively watched.
Mapping and Situational Awareness: Drones provide dynamic perspectives; integrating their data with mapping systems can be valuable. For instance, if a drone tracks a moving intruder, plotting that movement on a facility map in real time (based on drone GPS + the intruder’s position relative to drone) could guide ground teams. Some systems allow drones to create or update maps – like using a drone to do a quick scan and generate a 3D model of an area if something changed (like after an explosion or earthquake, for instance, to assess damage). That data can then be fed to crisis management tools. While not everyday use, in an integrated security architecture, having that capability ready is beneficial for resilience.
Data Fusion: Combining drone data with other sensor data yields richer intelligence. For example, if an acoustic gunshot sensor triggers in a campus, linking that with a drone’s thermal scan can pinpoint if someone is running away from the flash point. Or combining access logs with drone video might show, say, an unauthorized person tailgating through a door, and the system could highlight that sequence.
Security Directors along with IT should plan a data workflow: from collection (drones capturing data) to distribution (who needs to see it live – guards on radios? SOC monitors? – maybe equip field guards with tablets to get drone feed when responding) to storage and analysis (what gets saved, for how long, and how to review it).
A major advantage of integrated data is the ability to do post-incident analysis and improvement. After any security incident (or even a drill), reviewing the drone footage alongside fixed camera footage and alarm logs provides a 360-degree understanding. Maybe you find that the intruder exploited a blind spot – the drone saw him but only after a delay. That might lead to changing the drone patrol pattern or adding a fixed camera there. Or maybe analytics show that every night around 2 AM, the drone sees movement in a certain alley – investigating that could reveal a recurring vulnerability. These insights allow continuous refinement of security protocols.
Compatibility and Standardization: It’s wise to choose technologies that support common standards for data formats (like video in RTSP, telemetry in MISB compliant metadata if doing any military-grade tracking, etc.). Avoid proprietary ecosystems that trap your data. If your drone’s data can be exported easily, you can feed it into whatever analytics or archiving system you prefer.
One emerging concept is using cloud-based command centers, where drone data, fixed sensors, and even emergency communications come to a cloud platform accessible from anywhere. This could be useful for companies with multiple sites – a central corporate security center could oversee drone operations at all sites via cloud integration. Of course, that requires robust connectivity and trust in cloud security.
IT Collaboration: Integration is not purely a security department task – it’s an IT project too. Security teams should involve IT early to address network requirements (drones might use Wi-Fi or LTE to send video – ensure adequate coverage and bandwidth), to implement APIs between systems, and to manage any servers or cloud instances needed. As noted in Cuneo’s approach, bridging physical and cyber security is critical (Author: cuneosecurity – Cuneo Consulting). Drones are IoT devices; they should be inventoried in the IT asset list, their firmware kept updated (which might involve connecting to vendor sites), and their connections monitored for cyber threats (Do Drone Users Care About Data Security – DRONELIFE) (as drone data could be sensitive, one wouldn’t want a hacker tapping into the drone feed).
Compatibility and System Planning for Security Directors and IT Teams
When adding drones, planning for compatibility with current and future systems is important to avoid expensive retrofits or data silos. Here’s a checklist of considerations:
- Network Infrastructure: Ensure your Wi-Fi or private LTE network can handle drone communications. If using Wi-Fi, drones may go beyond existing coverage zones – you might need extenders or dedicated access points outdoors. Some enterprise drones create their own mesh networks; coordinate that with IT to prevent interference with other wireless systems. If drones use the cellular network (some come with SIM cards for control/video), make sure you have coverage and think about data costs and security (VPNs might be used).
- API Availability: Check what integration hooks are provided by the drone platform. Is there an SDK or API that allows you to send it commands or receive status? Many enterprise drones (e.g., those by DJI, Skydio, Parrot, etc.) have SDKs. Ensure your integrator or IT can work with those if custom integration is needed. Likewise, see if your existing security software has APIs or plugins for drones.
- Scalability: Today you might have one drone per site; in future maybe many or larger operations. Choose solutions that can scale. For instance, a small NVR can handle 16 cameras – if you add drones it might need an upgrade. Plan headroom for adding drone feeds. If using a cloud VMS, make sure adding a drone feed won’t blow through your license or storage limits.
- Interoperability Testing: Before fully relying on integration, do tests. Simulate an alarm and see if the drone triggers correctly, check that video latency in VMS is acceptable, etc. Work out any kinks. Sometimes devices technically integrate but have quirks (e.g., the drone video might not have the correct timestamp in the VMS). Iron those out with IT help.
- User Interface Training: If integration results in new UI elements (like a drone control panel in the SOC), train the team on that integrated interface. Possibly have joint drills where the security team and IT support respond together to ensure all tech works as intended under stress.
- Vendor Support and Partnerships: Work with reputable vendors who have experience integrating their systems. Some security integrators specialize in drone integration – consider consulting them or hiring such expertise. The FAA (if in the U.S.) also encourages integration for security especially for critical infrastructure, so there might be user groups or forums where you can learn best practices.
Unified SOPs and Governance: Once integration is in place, update your Standard Operating Procedures to reflect it. For example, the alarm response SOP should now include checking drone feed. The maintenance SOP should include IT checking the integration health periodically (like ensuring the API connection hasn’t broken). Define clearly who has authority to launch drones in automated scenarios – perhaps requiring a human confirm for certain triggers to avoid false dispatch (though automatic for some like perimeter breach might be fine).
Security Directors should also ensure that any integration respects regulatory boundaries. For instance, if your drones share video across state lines or international, know data export laws. Also consider ITAR (if your company deals with regulated tech, even drone footage of certain facilities might be sensitive).
Example of Integration in Practice: Think of a “security incident timeline” with integrated tech:
- 00:00 – Fence sensor triggers at north perimeter.
- 00:01 – Alarm system sends event to integrated security platform, auto-alerting guard on duty’s tablet and triggering drone dispatch.
- 00:02 – Drone launches; alarm event pops up on SOC dashboard with a map. The nearest PTZ camera auto-rotates toward the alarm location, and its feed plus a placeholder for the drone feed is displayed.
- 00:03 – Drone arrives; its thermal camera shows a person hiding by the fence. The system’s AI flags “person detected” and notifies operators with a red bounding box on the screen (Navigating Modern Security Challenges: The Crucial Role of Physical and Surveillance Security Solutions – Cuneo Consulting). This video is now recording on the VMS.
- 00:04 – SOC operator uses integrated audio to trigger a pre-recorded message over a loudspeaker at that zone (or if the drone has a speaker, the operator uses it: “Security, remain where you are”). Meanwhile, nearby ground officers are moving to intercept, guided by the intruder’s location from drone.
- 00:06 – Intruder is detained by guards. SOC marks incident resolved. The system automatically tags the drone video segment and related camera footage with the incident ID and archives it.
- 00:10 – Supervisor reviews the multi-source footage to debrief and creates a report. The integrated log shows alarm -> drone launch -> detection -> response, illustrating how quick it was.
In that scenario, everything was integrated so smoothly that the event was handled in minutes with evidence captured, and minimal manual steps beyond the guards physically arresting the intruder. That’s the ideal of integration.
By focusing on integration, an organization ensures that drones act as cohesive parts of a security ecosystem, multiplying effectiveness through synergy with other measures. The drone essentially becomes another sensor and responder in the network – albeit a very capable one. Achieving a unified security ecosystem with drones will pay dividends in efficiency and situational awareness, making the entire security posture stronger and smarter.
Mastering Regulatory Compliance and Ethical Considerations
Deploying drone surveillance in corporate security isn’t just a technical and operational challenge – it also requires navigating a complex web of regulations, legal requirements, and ethical issues. This section delves into the crucial compliance aspects: from aviation laws (like FAA Part 107 and beyond) to state and local privacy rules, and the ethical guidelines that should govern drone use. We will break down the key regulatory constraints (e.g., where and how you can fly, pilot certification, airspace authorization) and provide practical advice on working within those rules – including tips on handling FAA waivers for advanced operations like Beyond Visual Line of Sight (BVLOS). We’ll also discuss how to address privacy concerns proactively, ensuring that your drone program respects individuals’ rights and doesn’t expose the company to liabilities. Insurance, liability, and risk management will be covered as well, since flying drones carries responsibilities for safety. Finally, for compliance officers, we suggest resources like checklists and process templates to systematically keep your drone operations on the right side of the law and ethical practice. Mastering this area is not just about avoiding fines or lawsuits – it builds trust with employees, the public, and regulators, which is essential for the long-term viability of a corporate drone program.
Navigating FAA Regulations (Part 107, BVLOS, and Airspace)
In the United States, the Federal Aviation Administration (FAA) sets the rules for commercial drone operations. Corporate security use of drones squarely falls under commercial operations, which are governed primarily by 14 CFR Part 107 (commonly just called “Part 107”). Key points of Part 107 relevant to corporate security are:
- Remote Pilot Certification: Anyone operating the drone (or supervising its autonomous flight) must hold a Remote Pilot Certificate with a Small UAS rating (FAA Drone Regulations for Commercial Drone Use: Guide to New Drone Laws and Part 107 FAA Drone Rules | DARTdrones UAV Pilot Training). This involves passing an FAA exam on drone regulations, airspace, weather, etc. As a security manager, you should ensure all your drone operators are Part 107 certified (or are under direct supervision of someone who is, as allowed by rule). This certification must be renewed every 24 months (by passing a recurrent knowledge test or training). Building this into your training program is essential for compliance.
- Registration: Drones weighing more than 0.55 lbs (which is basically any decent security drone) must be registered with the FAA before flying under Part 107. The registration number must be marked on the drone. This is a simple online process but don’t overlook it – fines can apply for unregistered aircraft. If your company has multiple drones, consider using your company name for the registration and keeping a record of registration IDs. (Law enforcement can ask for proof of registration if they ever inspect your operations.)
- Operational Restrictions:
- Visual Line of Sight (VLOS): Under Part 107, the drone must remain within the visual line of sight of the pilot or a designated visual observer at all times (The FAA’s de facto drone privacy standards | IAPP). This typically means you cannot fly beyond how far you can see it with the naked eye (binoculars can’t be used to extend vision for compliance, although you can momentarily use them for identifying an object). For practical security use, this might restrict how far across a facility you can go unless you move with it or have observers. Many companies mitigate this by training additional staff as visual observers stationed strategically or accompanying the pilot (FAA Drone Regulations for Commercial Drone Use: Guide to New Drone Laws and Part 107 FAA Drone Rules | DARTdrones UAV Pilot Training) (FAA Drone Regulations for Commercial Drone Use: Guide to New Drone Laws and Part 107 FAA Drone Rules | DARTdrones UAV Pilot Training). If you want to go beyond VLOS, you’d need a waiver (more on that soon).
- Altitude Limit: Drones cannot fly higher than 400 feet above ground level (AGL) unless within 400 feet of a structure and not above 400 feet above that structure’s immediate uppermost limit (FAA Drone Regulations for Commercial Drone Use: Guide to New Drone Laws and Part 107 FAA Drone Rules | DARTdrones UAV Pilot Training). For most corporate campuses, you won’t need to go near that limit – typical security operations are well under 200 feet AGL for good visibility. But if you have high-rise buildings, note the exception: you can inspect a 1000-foot skyscraper by flying up to 1400 feet AGL as long as you stay close to it. Usually, though, staying low is beneficial for surveillance detail. In compliance terms, ensure any altitude pre-sets in your drone software are capped at 400 ft unless you have a specific FAA waiver.
- No Flying over People: Part 107 originally prohibited flying over any persons not directly participating in the drone operation, for safety (The FAA’s de facto drone privacy standards | IAPP) (The FAA’s de facto drone privacy standards | IAPP). However, a recent rule update (early 2021) introduced a more nuanced approach with drone categories that if met, allow operations over people under certain conditions. But as a baseline: You should avoid flying drones over crowds or uninvolved employees unless you have a drone that fits those new categories (for example, Category 1 drones are very small and have no exposed rotating parts that can injure skin – not likely applicable to larger security drones). For corporate security, this means if there’s a crowd of employees at an outdoor event, you should be careful. Either fly at a safe offset or altitude where a failure would likely not hit them, or get everyone “participating” by notifying them (though practically, that doesn’t make them participating). It’s a grey area improved by new rules, but caution is best.
- Daylight Operations: By default, Part 107 allowed operations in daylight or civil twilight (30 min before sunrise/after sunset) with anti-collision lights. As of the 2021 rule changes, flying at night is allowed if the pilot has taken updated training and the drone has anti-collision lighting visible for 3 miles (The FAA’s de facto drone privacy standards | IAPP). So, night operations are now part of the rule (no longer requiring a waiver), but you must have proper lights. For security, you will definitely want to fly at night, so equip your drones with approved anti-collision strobes (usually flashing red or white lights). Train your pilots on the updated night operation knowledge (the FAA made this a free online training for existing pilots). Once those are done, you’re compliant to fly at night. Remember to use the lights – it’s both a rule and a good idea to let other airspace users see the drone.
- Multiple Drones/Pilots: One pilot cannot operate multiple drones at once under Part 107 (FAA Drone Regulations for Commercial Drone Use: Guide to New Drone Laws and Part 107 FAA Drone Rules | DARTdrones UAV Pilot Training) (FAA Drone Regulations for Commercial Drone Use: Guide to New Drone Laws and Part 107 FAA Drone Rules | DARTdrones UAV Pilot Training). Also, you can’t have one drone operated by two pilots at the same time. In security terms, this means if you have 2 drones airborne, you need 2 certified operators (or one operator and one under direct supervision). Plan your team accordingly – don’t try to have a single pilot controlling a swarm (without a special waiver).
- Yielding Right of Way: Drones must yield to all manned aircraft (The FAA’s de facto drone privacy standards | IAPP). In practice, if a helicopter or low-flying plane approaches, your operations must ensure drones get out of their way. This rarely conflicts in typical low-altitude campus use, but if near helipads or hospitals, be vigilant. Observers should listen for aircraft and you should program any “Return Home” to not ascend too high if near approach paths.
- Airspace Authorization: Airspace in the US is classified (Classes B, C, D, E around airports). Under Part 107, drones can operate in Class G (uncontrolled) airspace freely, but to fly in controlled airspace (around many airports), you need permission. This is handled either via the FAA’s LAANC system (Low Altitude Authorization and Notification Capability) for many airports which gives near-instant approval through an app (UAS Data Exchange (LAANC) | Federal Aviation Administration), or via a manual application for others. For example, if your corporate HQ is 3 miles from a major airport, you’re likely in Class B or C and must use LAANC to get a clearance to fly at specific altitudes. The good news is many authorizations are automated and fairly quick (LAANC can give a response in seconds to minutes via approved apps). You’ll likely only get a certain max altitude allowed – e.g., in some zones maybe only up to 100 ft AGL. Compliance means checking the FAA UAS Facility Maps or using a LAANC app every time or getting a standing authorization.
- Tip: The FAA can grant “wide-area” or long-term authorizations for certain airspace via DroneZone application. If you frequently operate near an airport, apply for a blanket authorization (like “daily operations in Class D airspace near XYZ airport up to 200 ft”). This saves hassle in the long run.
- Also note Temporary Flight Restrictions (TFRs): e.g., if there’s a presidential visit or big sporting event near your site, a drone TFR might pop up. Always check sources like FAA NOTAMs or use apps (like B4UFLY or Aloft) to ensure no TFR blocks your flight at that time.
- Remote ID: A new rule (as of 2023) requires drones to broadcast identification information (like an electronic license plate). As an operator, ensure your drones either have built-in Remote ID or use an add-on broadcast module by the compliance deadline (September 2023 for operators). This means law enforcement can identify your drone’s registration number and your control station location if they detect it. For corporate security, this is double-edged: it adds transparency (which can be good for accountability), but also means if you are flying covertly, someone with the right scanner can see a drone is up and registered to your company. However, compliance is mandatory, so plan to comply. Keep documentation of your Remote ID module serials and such in your records.
- Waivers for Advanced Ops: Part 107 has a waiver process for operations that normally aren’t allowed. Common waivers relevant to security:
- BVLOS (Beyond Visual Line of Sight): If you want to legally fly beyond the pilot’s sight (e.g., to cover a huge campus or patrol a long pipeline without multiple observers), you need a BVLOS waiver. These are not easy to get – the FAA wants to see robust detect-and-avoid systems or other mitigations. However, companies like railroad and security firms have been testing ground-based radar or visual systems to help with BVLOS. If your corporate environment is relatively contained (private property with few other aircraft), you can make a case. Another approach: use a network of observers with handoff procedures as per line-of-sight rules to effectively go farther (that doesn’t require a waiver if done right).
- Operations Over People: If you foresee needing to routinely fly over people (like events), you could apply for a waiver if your drone has been proven safe (e.g., parachute-equipped drones have gotten waivers). With the new rule categories, waivers might be less needed if you buy Category 2 or 3 compliant drones for operations over people (these have to meet certain impact energy standards).
- Multiple drones per pilot: Some security scenarios (like an automated swarm responding together) would need a waiver for one pilot, two+ drones. Currently, that’s rare and experimental.
- Moving vehicles: Part 107 also restricted flying over moving vehicles. If you want to, say, follow a car down a road on your property, technically that’s restricted unless you get a waiver or ensure no one is in the vehicle or it’s on your closed property. For the most part, this might not need a waiver if on private roads with authorized participants (like your security vehicles who are aware).
- State and Local Drone Laws: Beyond FAA, some states have additional laws. For example, some states restrict drone surveillance of private individuals or critical infrastructure without consent. As a corporation, ensure your use doesn’t inadvertently violate, say, anti-voyeurism laws – generally if you stick to your property and security purposes, you’re fine, but be aware of peeping tom laws or any local statutes about drones. Also, some cities have park or city property bans – not directly applicable on your campus, but if you ever let the drone wander out, you should know them. The key is: FAA governs airspace, but privacy and land use aspects can be state domain. A compliance officer should review your state’s drone laws (around 2017, more than 40 states were considering such laws (Drones: Aren’t the Laws Already on the Books? | IAPP), many focusing on privacy and critical infrastructure).
- International Regulations: If your corporate operations are global, note that other countries have their own rules (often similar but with differences). For example, the EU has EASA regulations, dividing drones into categories (Open, Specific, Certified) with different requirements. Canada requires certification akin to Part 107 as well. Always localize your compliance approach – what’s fine in Texas might need a permit in Tokyo.
In summary, build regulatory compliance into the program from day one:
- Maintain a binder (or digital folder) with copies of all pilot certificates, drone registrations, waivers, insurance documents, and any required logbooks.
- Develop a pre-flight checklist that includes checking airspace and weather, and verifying any needed authorizations like LAANC are obtained.
- Incorporate rules into training: e.g., pilots must call out when visual line of sight is in jeopardy, or have a protocol if passing control to another pilot (if moving across a large area).
- If using contractors or third-party service providers for drone ops (some companies hire drone security services), ensure they follow these rules too and have necessary paperwork – ultimately the responsibility might still reflect on you as the site operator.
By rigorously following FAA rules, you not only avoid fines (which can be in the thousands per violation) but also improve safety. Every regulation is fundamentally about ensuring drones don’t pose undue risk to other aircraft or people on the ground. A single accident could jeopardize your whole program (and be a PR issue), so compliance is non-negotiable.
Privacy, Surveillance Limits, and Ethical Use Policies
Beyond aviation rules, privacy and ethics form the other critical dimension of compliance. Flying a camera in the sky raises understandable concerns about surveillance overreach. Corporations must proactively address these to maintain trust and avoid legal trouble. Here’s how to navigate privacy and ethical considerations:
Understand Privacy Laws and Expectations:
- As mentioned, the FAA explicitly does not regulate privacy (The FAA’s de facto drone privacy standards | IAPP), so that falls to state laws and general rights. Many states have laws against using drones to surveil individuals where they have an expectation of privacy (like peering into someone’s backyard or window). On your corporate property, you generally have more leeway to surveil for security since it’s private property of the business. However, employees and visitors also have some expectation that they aren’t personally spied on beyond security necessity. Ethically and legally (in terms of employment law or union agreements, perhaps), you should define the scope of drone monitoring.
- Transparency: Best practice is to be transparent that the facility uses drone surveillance. Include it in privacy notices or signage: e.g., signs at entrances: “Security Notice: This facility employs video surveillance, including CCTV and occasional drone patrols.” This way, people are informed – an important aspect of privacy norms and often legal compliance (some states require posting if audio or video surveillance is present).
- Data Minimization: Only collect what you need. If your drones are recording 24/7 but you only use footage when incident happens, consider not recording continuously in sensitive areas to minimize data on people’s daily activities. Perhaps only live-monitor there and record on trigger. Or use resolution in such a way that individuals aren’t identifiable except when zoomed in during a security event. These are “privacy by design” techniques.
- No Harassment or Discrimination: Ensure drones are not used in a way that targets individuals for non-security reasons. For instance, do not use a drone to follow an employee around because a manager is curious about their productivity – that veers into unethical surveillance. The drone program should be squarely for safety and security (protecting assets, life, property from harm), not general employee monitoring. In fact, coordinate with HR on this boundary, and possibly mention in employee handbooks how drone surveillance is and isn’t used.
- Avoid Sensitive Areas: Steer clear of places where privacy is expected – e.g., don’t hover near office windows where you might see inside restrooms or break areas unnecessarily. If your campus borders residential areas, geofence your drones to not overfly the neighbor’s yards or apartments. We saw in IAPP insights that drones heighten privacy concerns because of their vantage (Why Privacy Pros Should Be Engaged With Drone Regs | IAPP). Showing that you intentionally avoid spying on non-company areas will help maintain community trust. Several states (like California) treat drone intrusion the same as if a person trespassed for peeping – so never linger over someone else’s private property without strong justification (and usually, there is none in corporate security).
- Audio Surveillance: Generally, avoid recording audio with drones. Recording audio without consent can violate wiretap/eavesdropping laws. Most drones don’t carry sensitive mics for that (their own propeller noise usually drowns distant audio anyway). It’s best to ensure any recording device on the drone is video-only. If you do employ something like a gunshot detection mic, ensure it’s used only for that specific sound and not general audio recording (and legally, some states even consider that a form of eavesdropping – check local laws).
- Third-Party Data Use: If you contract with a security company that operates drones for you, ensure the contract specifies that they cannot use or share the video data for any purpose other than your security, and they must protect it. You don’t want them posting a “cool intruder video” on YouTube that came from your site, for instance, or selling data on employee movements (which is unlikely, but contractually lock it down).
Implement an Ethical Use Policy: Just like IT departments have acceptable use policies for computers, have an acceptable use policy for drones. Outline what they will and won’t be used for. For example:
- Only trained and authorized security personnel may operate or task the drones.
- Drones will be used only to observe and safeguard company property and the people on it, and only in ways consistent with law and respect for privacy.
- Prohibited uses: spying into private areas, personal errands, harassing individuals, etc.
- How footage will be handled: e.g., “Drone footage is considered confidential security information. It will be stored securely and accessed only by authorized personnel for legitimate security purposes or investigations. It will be retained for X days unless needed longer for an investigation, then deleted.”
- Any sharing: “Video may be shared with law enforcement if relevant to a criminal incident, but not publicly released except as required by law.”
- Ensure compliance with policies like GDPR if in Europe – in EU contexts, using drones might mean you need a Data Protection Impact Assessment (DPIA) since it can be high risk processing of personal data. You would also need a lawful basis for processing under GDPR – likely legitimate interests of security, and you must balance that against privacy rights.
- Under GDPR and similar, people have rights to know about and possibly even see data about them. In a workplace, this can get tricky. It’s one reason to not retain more data than needed.
Engage Stakeholders:
- Employees: It’s smart to communicate with employees about the introduction of drones. Emphasize the safety/security rationale and what measures you’ve taken to respect their privacy (for instance, “the drones will focus on external threats and are not there to watch employees working or take the place of our trusting workplace environment.”). If there’s a works council or union, engage them early to get buy-in. Perhaps create a written policy with their input that everyone acknowledges. As noted in an IAPP piece, there’s initial public skepticism and fear of drones (Why Privacy Pros Should Be Engaged With Drone Regs | IAPP), but transparency and experience can alleviate that.
- Public/Community: If your drones might be visible to neighbors or the public, consider a PR communication or at least have prepared talking points. E.g., if a local newspaper sees drones over the corporate park and wonders if you’re spying on the town, you can clearly state: these drones operate only within our property for security, here’s how we ensure privacy, etc. Getting ahead of such concerns fosters goodwill. Privacy advocates like Electronic Privacy Information Center (EPIC) have raised concerns when FAA didn’t mandate privacy standards (The FAA’s de facto drone privacy standards | IAPP), so companies should self-regulate to avoid becoming examples of “bad” surveillance.
- Compliance Training: Ensure that your drone operators and security team are trained on privacy do’s and don’ts as much as they are on flight skills. For example, a pilot might be curious and zoom in on something not relevant – they should resist that urge unless there’s a security reason. That’s part of professional ethics training. Maybe incorporate scenario-based training, e.g., “What do you do if the drone inadvertently captures footage of employees in a sensitive situation or off-duty? (Correct answer: don’t circulate it, report it to security management if necessary, then ensure it’s deleted if not needed.)”
- Incident Response and Privacy: If a drone does capture something sensitive (imagine it caught an employee doing something embarrassing on break), handle that carefully – treat it as private except if it involves wrongdoing. Many companies in general security have a policy to not point cameras in certain places – with drones one must be dynamic, but you can still have rules like not hovering around the outdoor smoking area zooming in on personal conversations, for instance.
Insurance and Liability:
- Make sure your insurance covers privacy breaches or inadvertent surveillance mistakes. Some liability insurance might cover “personal and advertising injury” which includes invasion of privacy, but check the fine print. Drones often need special insurance riders anyway for aviation liability and property damage coverage.
- Liability for accidents: Ethically, you must ensure safe operation. A falling drone can injure someone – which could lead to negligence claims if you didn’t follow safety guidelines. Always have pre-flight checks and maintenance done to minimize chances of mechanical failure. As part of compliance, keep flight logs. If an incident does occur, those logs can show you were in compliance (e.g., you kept VLOS, you weren’t over people, it was an unforeseeable malfunction).
- Inter-agency Coordination: If you plan to fly in areas where law enforcement might be concerned (e.g., near critical infrastructure or in city jurisdictions), sometimes letting local police know of your program prevents misunderstandings (like someone calling 911 about a suspicious drone and cops thinking it might be malicious – if they know it’s likely yours because you informed them, that can help). Some police departments appreciate being looped in; plus, if you ever need to use your drone footage as evidence, having them aware of the program and its integrity can help credibility.
Example of Ethical Policies in Practice: One large tech company introduced drones with a strict mandate: they will only be used in emergencies or specific patrol routes away from building windows. They set up geofences so drones physically could not approach certain sensitive office areas. They also allowed employees to opt-out if they had religious or deep personal concerns about being filmed from above (in practice, they just ensured those employees’ work areas were in covered zones or that they weren’t individually tracked). These measures were above and beyond legal requirements, but it maintained a trust that the company cared about employee privacy. Additionally, they engaged the union with test demonstrations to show exactly what the drone sees (and more importantly, what it can’t easily see, like through tinted windows, etc.) to demystify it.
As a result, after initial wariness, the drones became an accepted part of security, no different than a guard walking by – because people knew it’s all for safety and there were guardrails in place to prevent misuse.
Compliance Checklist for Privacy & Ethics: It may be useful to develop an internal checklist or even a Privacy Impact Assessment (PIA) for your drone use. Consider:
- Purpose specification (why using, what scenarios, is it necessary?),
- Data flows (what’s captured, stored, viewed by whom, for how long),
- Risk analysis (risks to individuals’ privacy and how you mitigate),
- Measures (signage, policies, technical controls, training),
- Review and audit (periodically audit drone footage to ensure no policy violations, and allow an internal ethics or compliance officer to do spot checks on usage patterns).
Keep in mind what one privacy article noted: drones bring surveillance into public awareness more dramatically (Why Privacy Pros Should Be Engaged With Drone Regs | IAPP). Your corporate ethical stance on drone use can set a tone in the industry and with your staff.
Downloadable resources: perhaps provide a template for a Drone Privacy Policy or Compliance Checklist. For instance,
- “Obtain Part 107 certs for all pilots – Completed.”
- “Register drones with FAA – Completed.”
- “Add drone coverage to insurance – Completed.”
- “Post surveillance notice signage – Completed.”
- “Train operators on privacy restrictions – Completed.”
- “Establish data retention limit: 30 days – Implemented in VMS.”
- “Perform annual review of drone footage usage – scheduled.”
By being thorough on these fronts, your drone program will not only be legally compliant but also ethically sound. This fosters support from all stakeholders and reduces the risk of backlash or legal action. Ethical practices essentially future-proof your program by making it resilient against external scrutiny. As one ASIS article suggested, clear guidelines and collaboration with policymakers are vital as drones become widespread (The Rise of Drones and Counter-Drone: A Double-Edged Sword in …) – within your company, treat yourself as the policymaker that sets those guidelines clearly now.
Insurance, Liability, and Risk Management
Flying drones introduces certain risks, and part of compliance is making sure you can financially and procedurally handle those risks. Let’s cover how to manage the liability aspect:
Insurance Coverage:
- Liability Insurance: Verify that your corporate insurance covers drone operations. Many general liability policies now can include coverage for unmanned aircraft, but you might need to add it or get a separate policy. This typically covers bodily injury or property damage to third parties caused by the drone. For example, if a drone crashes through a car windshield in the parking lot, liability insurance would pay for repairs and any injuries. Without coverage, the company would pay out of pocket and possibly face lawsuits. Some insurers have specific requirements (like pilots must be certified, etc.) for coverage to apply – ensure compliance with those too.
- Hull Insurance: This covers damage to the drone itself (like comprehensive auto insurance). If you have expensive drones, consider it. If a drone is lost or destroyed, hull insurance can replace it. If cost is small (sub-$5k drones), some companies just budget replacements rather than insure each, but if you have a fleet or high-end gear, it’s wise.
- Privacy/Personal Injury Insurance: As mentioned, some policies have personal injury coverage which includes invasion of privacy or defamation. Check if drone usage could trigger those (like if someone claims your drone violated their privacy and sues). It might fall under that category. If not covered, see if an umbrella policy can or if needed at all (depending on local laws – in some places individuals can sue for privacy invasion as a civil tort; your company should be defended by insurance ideally).
- Workers’ Comp: If an employee is operating a drone and gets injured (maybe a battery fire or something), normal worker comp covers it, but nothing special needed.
- Errors & Omissions: If providing drone surveillance as a service to third parties (not likely in internal corp scenario), you’d consider professional liability. But for internal, not applicable.
Liability Considerations:
- Who is liable if your security drone accidentally falls on a neighbor’s property and causes damage? Generally, your company as the operator is liable. If the cause was manufacturing defect, you might pursue the manufacturer, but the third-party will come after you. That’s why having insurance is key.
- There’s also non-physical harm liability: if someone claims your drone operations violated their rights. For example, an employee claims harassment or emotional distress because a drone followed them. Ensuring policies are followed will help in defense (and insurance in case they litigate).
- If you integrate drones with alarms, consider liability if the system fails to respond to an alarm – for instance, if an incident occurs and someone argues that relying on a drone delayed direct guard response. This is more theoretical, but be prepared to justify your processes.
Risk Assessment and Mitigation: Before launching the program, do a formal Risk Assessment:
- Identify risks: Drone crash, loss of control, entering no-fly airspace, privacy complaint, pilot error, battery fire in office, etc.
- Rate their likelihood and impact.
- For each, define mitigation:
- Crash -> mitigate by thorough training, maintenance, not flying over people/cars, having emergency procedures (like a dedicated emergency landing zone plan if issues).
- Loss of control (flyaway) -> mitigate by geofencing (so it can’t run off too far), setting up return-to-home properly, having a pilot ready to take manual control from automation at any sign of trouble.
- Entering restricted airspace (like accidentally into a nearby airport space) -> mitigate by pre-programming max boundaries, using software that integrates with geo-awareness, and always checking LAANC.
- Privacy complaint -> mitigate by the policies and transparency discussed.
- Pilot error (like hitting wrong button) -> mitigate by simulation training and perhaps using systems with obstacle avoidance.
- Battery fire -> store/charge batteries in a fire-safe bag or cabinet, train staff on handling LiPo batteries (don’t overcharge, don’t use damaged ones).
- Data breach (drone footage hacked) -> encrypt data links, use secure networks.
- Acceptable risk vs. residual risk: Decide what level is acceptable. Perhaps you accept minor risk of property damage in exchange for security benefit, but not risk to human life, so you plan flights such that even a worst-case crash is unlikely to severely injure (like avoiding flying directly over gatherings or at high altitudes from which a fall is deadly).
- Create an Emergency Procedure: If a drone goes down, what do you do? (First aid if anyone injured, secure the crash site, notify FAA if required – Part 107 says if serious injury or property damage over $500, you have to file an accident report to FAA within 10 days (FAA Drone Regulations for Commercial Drone Use: Guide to New Drone Laws and Part 107 FAA Drone Rules | DARTdrones UAV Pilot Training)). Also if drone is lost on neighbor’s property, how to retrieve (coordinate politely, maybe have info on drone so they can return it).
- Plan for Cybersecurity incidents too: What if someone tries to jam or hack your drone? Jamming GPS or control signals is illegal, but could happen (we have to consider insider threats or activists). Have a procedure if you suspect interference – likely land immediately and cease operations until resolved. Use equipment that hops frequencies or is encrypted to mitigate hacking. Keep drone firmware updated as those patches often close security holes.
Legal Coordination:
- Inform your legal department of the drone plans so they can advise on any liability waivers needed (for example, if the drones might inadvertently capture some personal data, do you need any disclaimers?).
- If you have contracts with security vendors or third parties that come on site, consider adding clauses about drones – e.g., they must not interfere with them, or you might share footage with them if needed and under NDA.
Compliance Documentation:
- Keep detailed records of flights, incidents, maintenance. If an accident happens, being able to show logs of maintenance and pilot training will help defend against negligence claims (like how airlines show they maintained the plane properly in crashes).
- If you do any incident investigation using drones, document that you used it in accordance with policies (no fishing expeditions beyond scope, etc.).
Downloadable Compliance Checklist (continued): For this section, maybe an insurance and legal checklist:
- Consulted insurance broker on drone coverage – ✅
- Obtained $X million UAV liability coverage – ✅
- Registered with state if required (some states require registering with state DOT as well) – ✅
- Completed risk assessment and filed with risk management – ✅
- Established emergency/accident protocol – ✅
- Trained pilots in emergency procedures and reporting – ✅
- Verified compliance with OSHA (if any OSHA guidelines about drones – not specific yet, but general workplace safety rules) – ✅ (for example, instructing that no one should try to catch a drone by hand – a common-sense but worth stating rule to avoid injury).
- If in critical infrastructure sector, complied with any sector-specific guidelines (like DOE guidelines for drones at power plants, etc. – some industries have recommended best practices, e.g., ASIS might have something for security applications, check those) – ✅
The bottom line: treat the drone program with the same seriousness of compliance as you would a new vehicle fleet or a new IT system handling sensitive data. Cover your bases legally, ethically, and with insurance. Doing so not only avoids trouble but also instills confidence in upper management that the program is professional and controlled – making them more likely to support and invest further in it.
UAS Facility Maps
UAS Facility Maps show the maximum altitudes around airports where the FAA may authorize part 107 UAS operations without additional safety analysis. https://www.faa.gov/uas/commercial_operators/uas_facility_maps
By mastering this matrix of regulations and ethics, your company not only stays within the law but shows leadership in responsible drone use. In a field as new as drone surveillance, those who set a high compliance bar are effectively shaping industry norms and demonstrating that technology can be adopted without sacrificing safety or privacy. Now, with the legal and ethical framework in place, we can proceed to effectively implementing the program in a structured way, which is our next topic.
Developing and Implementing a Corporate Drone Program
Implementing a drone surveillance program in a corporate environment requires careful planning and execution. This section provides a step-by-step guide to developing your program from the ground up. Whether you’re starting with one drone or a fleet, following a structured plan will ensure you cover all critical aspects: from initial buy-in and pilot training to SOPs and ongoing performance monitoring. We’ll outline each phase – Assessment, Planning, Pilot Projects, Full Deployment, and Continuous Improvement – with key actions and tips. Special focus will be given to the practical management of the program: establishing Standard Operating Procedures (SOPs) for drone use, integrating drone ops into daily security routines, and risk assessments specific to drone flights. Templates for things like SOPs and risk assessments will be suggested (e.g., pre-flight checklists, incident reporting forms). We’ll also address how to involve stakeholders (like operations managers, IT, legal, and ground security teams) throughout the process to ensure the drone program complements and enhances existing security measures rather than disrupts them. By the end of this section, you should have a clear roadmap to go from concept to a fully functional drone surveillance unit that runs like a well-oiled machine day-to-day.
Step 1: Executive Buy-In and Program Definition
Any successful security initiative starts with clear objectives and leadership support. For a corporate drone program, articulate the goals and secure executive backing early on:
- Define Purpose and Scope: Outline exactly why you need drone surveillance. Is it to reduce response times to alarms, cover blind spots, augment guard patrols at night, secure a new large facility, etc.? Defining this will drive all other decisions. Set broad objectives (e.g., “reduce security incidents in perimeter X by 50%” or “achieve complete visual coverage of campus during off-hours”). Also determine scope: is this for one facility or multiple? Will it operate 24/7 or certain hours? Are drones going to be used only outside or perhaps inside large warehouses too? A clear scope prevents mission creep and sets the stage for resource planning.
- Develop a Business Case: Combine the ROI/TCO analysis from earlier sections into a proposal for leadership (Drone Industry Visionary Interview: Ryan Smith defines the tangible (and invisible) ROI of drone security | Commercial UAV News) (Security Drones: Benefits, Use Cases and ROI of Using Drones in the Security Industry). Include both quantitative benefits (cost savings, incident reduction metrics) and qualitative ones (improved safety, technological leadership). For example: “By implementing a drone patrol on our 200-acre site, we expect to save $X per year in theft reduction and reduced guard overtime, paying off the investment in Y years.” Also mention intangible value: quick aerial visuals can prevent business disruptions (like quickly finding a small fire before it becomes big). Use data like the fact that 92% of companies see ROI within a year (Security Drones: Benefits, Use Cases and ROI of Using Drones in the Security Industry) or Titan’s 60% cost saving example (Drone Industry Visionary Interview: Ryan Smith defines the tangible (and invisible) ROI of drone security | Commercial UAV News) to bolster argument.
- Executive Champion: Identify a senior executive (perhaps the CSO – Chief Security Officer, or a VP of operations) who will champion the program. Their support will help in resource allocation and in smoothing cooperation across departments. Present the plan to them emphasizing how it aligns with corporate security strategy and risk management. Often, linking it to risk mitigation of high-value assets or employee safety enhancements resonates at the C-suite level. Highlight that many forward-thinking companies are adopting this (so as not to be left behind in leveraging tech).
- Budget and Resources: At buy-in stage, be prepared with an estimated budget. Include equipment costs (drones, payloads, spares, charging stations), software (licenses for fleet management or integration, if any), training costs (training courses or time for pilots), and ongoing ops (maintenance, insurance, potential staffing). You might propose a phased budget: initial pilot costs, then scaling costs if pilot successful. Executives appreciate cost control, so showing a phased approach with review checkpoints can make them more comfortable approving.
- Alignment with Policies: Ensure you address how the program will comply with company policies and values (this shows you’ve thought of more than just the cool factor). For instance, if the company has a strong privacy ethos, mention the privacy safeguards you’ll implement (The FAA’s de facto drone privacy standards | IAPP) (Why Privacy Pros Should Be Engaged With Drone Regs | IAPP). If safety is a core value, show you have training and compliance to ensure safe operations. This all helps in getting not just approval, but active support.
- Timeline: Provide a high-level timeline for implementation – e.g., “Q1: Planning and procurement, Q2: Training and pilot deployment, Q3: evaluation and scaling, Q4: full operation.” This sets expectations and shows you have a plan.
At this stage, you don’t need every detail (that comes next), but you need enough to answer: Why are we doing this? What do we need? What’s the return? And how will we do it responsibly?
Once you have executive buy-in (and likely a budget allocated), you can move into the detailed planning of the nuts and bolts.
Step 2: Assemble the Team and Conduct Training
With green light from leadership, put together the core Drone Program Team and ensure they have the necessary expertise:
- Program Manager: Assign a program manager (could be the security manager or a dedicated person) who will oversee the rollout. They coordinate between security, IT, legal, facilities, etc. This is the go-to person for everything drone-related and typically the one ensuring timelines and SOP development are on track.
- Pilots/Operators: Identify who will actually operate the drones. It could be existing security staff or new hires specifically for UAV operations. Many corporate security teams cross-train some officers as drone pilots so they can multitask. Choose people with aptitude for technology and strong attention to detail (maybe those with RC hobby experience or younger officers eager to learn tech). Ensure each candidate either has or will get the Part 107 license (in the US) (FAA Drone Regulations for Commercial Drone Use: Guide to New Drone Laws and Part 107 FAA Drone Rules | DARTdrones UAV Pilot Training). You might sponsor them through a training course or set up internal study groups. There are many online courses for Part 107, or you could hire a trainer. This is also time to decide how many pilots vs drones – ideally at least one primary and one backup pilot per drone, to cover shifts and absences. If 24/7 coverage is needed with a single drone, likely need multiple pilots across shifts (unless using a third-party service that monitors the feed overnight).
- Visual Observers: If operations will ever require observers (for beyond line of sight expansions or to watch in busy areas), incorporate that into team roles. Observers can be guards given additional training to spot the drone and hazards. It might not be a full-time role, but assign people when needed.
- Maintenance/Technical Support: Decide who will maintain the drones (battery charging, firmware updates, repairs). Train those people on the equipment – often the pilots do it themselves, but if your IT or facilities folks want to handle technical maintenance, coordinate that. Some orgs involve IT for software updates and security patches on the drone systems (especially if integrating with network).
- IT Integration Support: Have an IT point person to handle network setup, software integration, data management (ensuring storage and security of video). They should be part of the planning team early to line up any needed infrastructure (e.g., setting up a dedicated computer or tablet in the SOC for drone control, configuring network firewalls to allow drone controller comms, etc.).
- Legal/Compliance Advisor: Not necessarily a dedicated person on the daily team, but ensure your corporate counsel or compliance officer is consulted to review procedures (especially privacy, data retention, FAA compliance). They might help draft any necessary policy language or disclaimers. Also, if any waivers need to be filed with the FAA, legal should oversee or at least approve the formal documents.
- Training Program: Schedule formal training. This includes:
- Regulatory training: Part 107 exam prep (for US). For non-US, whatever local certification needed (e.g., EU Open category training, etc.). Provide resources or classes. Perhaps reimburse exam fees as needed. Everyone must understand the legal rules thoroughly.
- Flight training: Do practical training in a safe, open environment. Before deploying drones over your critical assets, practice in an empty field or a low-risk area of the campus. Start with manual flight basics: takeoff, hovering, maneuvering, emergency landing. Then practice the typical security maneuvers: following a fence line, orbiting a point of interest, switching between camera views (visual vs thermal), using the payloads (shining spotlight on a target, using loudspeaker).
- Consider hiring a professional UAV instructor or sending team members to a drone training academy for security applications. There are specialized courses now (some by ASIS or law enforcement bodies) on tactical UAS operation.
- If using advanced features (like automated patrol routes or tracking mode), practice those and also simulate things like loss of GPS or signal to ensure pilots can take over.
- Simulations and Drills: Use flight simulators if available – some drone manufacturers provide computer simulators that mimic the drone’s control and physics. It’s great for initial orientation without risk.
- Once basic proficiency is achieved, run mock security scenarios. For instance, have a person act as an intruder at location X and see how the drone team responds, integrating with ground security. This not only trains the pilots but also the coordination and communications. Debrief after each drill: what went well, what could improve.
- Safety and Etiquette: Train on pre-flight checklists, battery handling, what to do if something goes wrong (like how to safely crash-land away from people if needed). Emphasize not to push limits – e.g., if environment is unsafe (high winds, etc.), they have authority to cancel flight. Create a culture of safety first.
- Integration Training: If the drone feeds into SOC screens or if ground guards will use tablets to view drone video, train those personnel too. Everyone who interacts with the drone or its data should know how to do so. The more comfortable the whole security team is with drones, the better they’ll adopt and trust them. For example, train the radio protocol between drone pilot and ground patrol: the pilot might use call sign “Eye in the Sky” and relay suspect description and direction, etc. Practice that communication so it’s smooth.
- Standard Operating Procedures (SOP) Drafting: While training, concurrently start drafting SOPs (or at least outlines) for how the drone operations will be conducted. We cover that in the next step, but involve your new pilots in drafting – they will have practical insight from training on what works.
- Coordinate with existing security operations: Introduce the drones and team to the rest of the security staff through a briefing or demo. It’s important non-drone personnel understand the drone team’s role and don’t feel replaced or threatened. Emphasize it’s a tool to help them, not to monitor them. Encourage questions and get feedback – maybe a veteran guard will suggest good vantage points to launch from, etc. This fosters cooperation.
- Trial Runs: Before official go-live, do some trial patrols during a quiet period (e.g., a weekend) to test everything end-to-end with the actual team.
Throughout this, document everything: training hours, test results, issues encountered and solutions. This will be good for refining SOPs and also for showing compliance (e.g., if asked, you have proof all pilots underwent a certain amount of training beyond just passing a test).
By the end of Step 2, you should have a competent team ready to operate drones safely and effectively, and initial procedures drafted from their training experience.
Step 3: Establish Standard Operating Procedures (SOPs) and Policies
Step 3: Establish Standard Operating Procedures (SOPs) and Policies
With a trained team in place, the next critical phase is to develop Standard Operating Procedures (SOPs) that will govern all aspects of your drone program. SOPs ensure consistency, safety, and compliance. They also integrate the drone operations with existing security protocols so everyone knows what to do and what to expect. Start by drafting SOPs in the following areas:
- Pre-Flight Procedures: Detail the steps to take before any drone flight. This should include a pre-flight checklist – for example:
- Verify weather conditions are within acceptable limits (wind, precipitation, temperature).
- Check the drone’s battery is fully charged and in good health (and spares are ready).
- Inspect the airframe, propellers, and payload (camera, etc.) for any damage or loose parts.
- Ensure the firmware/software of the drone and controller are up-to-date and functioning.
- Confirm GPS connectivity and calibrate compass if needed.
- Check that the SD card or recording device has sufficient space (if recording).
- Test the controls and communication link (perhaps a short hover test in a safe area).
- Verify that required airspace authorization is secured if flying in controlled airspace (e.g., LAANC approval received for this flight) (UAS Data Exchange (LAANC) | Federal Aviation Administration) (UAS Data Exchange (LAANC) | Federal Aviation Administration).
- Confirm Remote ID broadcast is functioning (per FAA rules).
- Notify relevant security staff that a drone flight is about to commence (so guards or employees aren’t surprised).
- Flight Operations SOP: Lay out how flights are to be conducted:
- Define normal patrol routes or patterns. For example, “Drone 1 will conduct a perimeter sweep following the fence line at 50m AGL, moving clockwise, between midnight and 00:30, and then return to base.” If using autonomous waypoints, list the route or have it pre-programmed, but require a pilot to monitor.
- Specify communications protocol. Pilots should have a call-sign and communicate on the security radio channel. E.g., “Eye-One to Control: launching for perimeter patrol of Sector A.” and “Eye-One: intruder spotted at location X, continuing observation, ground units please respond.” Everyone should know those call signs and respond accordingly. If you have a central SOC, the operator there might direct the pilot where to look, etc. This should be scripted to avoid confusion (like using clear terms – “Proceed to Bravo Gate” vs “go over there”).
- Address manual override and autonomy: If using automated flight modes or pre-set routes, state that a pilot must be ready to take manual control at any moment if a hazard arises. Also note when it’s acceptable to use automated tracking (e.g., following a moving intruder) and when to avoid it (perhaps not over very uneven terrain or where lots of obstacles could confuse the system).
- Establish no-fly zones on your campus map. These might include areas above crowds (like an open-air cafeteria during lunch) or sensitive equipment (maybe avoid hovering directly over the corporate data center’s satellite dishes, etc., to prevent interference or risk of fall damage). The pilot should mark these and either software-geofence them or strictly observe them. If flight must occasionally go there (e.g., in emergency), note that it requires command authorization.
- Define standard altitudes and distances for typical tasks. For instance, normal patrol at 200 feet AGL for broad view, but drop to 100 feet for closer inspection if needed. Or, “do not approach a person within 50 feet vertically or horizontally unless necessary to communicate via loudspeaker,” to maintain a safety buffer.
- If you have multiple drones, detail how they will be separated or coordinated. (Maybe you won’t fly two in the same airspace sector, or one covers east campus, one west, etc., to avoid any mid-air conflict. Or if both need to converge, one flies higher than the other. Essentially an internal de-confliction rule set.)
- Visual observer roles: if you deploy observers, SOP should call for them in certain ops (like if going beyond a building out of pilot’s sight, station an observer on far side, who maintains radio contact).
- Loss of signal/GPS procedures: Most drones have Return-to-Home (RTH). SOP: ensure home location is set at takeoff, and if signal is lost, allow the RTH to engage (or specify that after X seconds of lost comms, the pilot will manually invoke RTH). Also, if GPS is lost but the drone is still controllable, pilot should immediately switch to ATTI mode (manual altitude/attitude control) if trained to do so and bring it back. Write these steps out so in the stress of the moment the pilot recalls the plan.
- Emergencies: e.g., if a drone is about to crash or does crash, prioritize safety of people – pilots should attempt to steer towards empty space. If something happens like the drone catches on fire (rare but lithium batteries can ignite), have a protocol (like use a fire extinguisher – and have one rated for electrical fires in the control area).
- Handover procedures: If one pilot needs to hand over control to another (say shift change mid-mission, or an observer takes control), describe how to do that safely (perhaps have the drone hover at safe altitude, confirm second pilot’s control link, then first pilot disengages).
- Post-Flight Procedures: What happens after each flight:
- A post-flight inspection of the drone for any new damage or wear (this helps catch hairline cracks, etc., before next flight).
- Rotate or charge batteries immediately after flight. Good SOP is to let batteries cool for 10-15 minutes, then charge (to preserve battery life). Have a station or procedure for that.
- Download any recorded footage if needed and store it per data management policy. Secure the data – e.g., at end of a shift, pilot offloads the video to the secure server and wipes the card. Or if using a streaming recorder, ensure it was properly archived.
- Log the flight in a flight logbook. Include date/time, pilot, purpose/mission, duration, any noteworthy events or issues (e.g., “battery cell warning occurred” or “observed interference near substation – will investigate cause”). Also log any payload use (e.g., used loudspeaker or spotlight).
- Maintenance triggers: if a flight was the 50th flight for that drone, maybe per maintenance schedule it needs a deeper inspection or part replacement – the log can note it’s due. Some SOPs say after every 10 hours of flight, check propeller tightness or motor condition, etc. Build those thresholds in.
- Secure the drone in its storage (especially if operations are done for the day) – meaning physically put it in a locked charging box or storage room to prevent tampering.
- Security & Privacy Protocols: Incorporate the ethical guidelines into SOPs so that operators are contractually and clearly bound to them:
- Define where drones should not purposely surveil. E.g., “Drones will not be used to hover outside building windows or to target individuals without a security reason. If camera inadvertently captures sensitive footage (e.g., employees in private areas), operators will cease viewing and report it to management for proper handling.”
- Include a requirement that any requests to use drone footage or live feed for non-security purposes (like a manager asking to see if employees are at their desks) must be denied or escalated to the CSO for approval in line with policy. Essentially empower your operators to say “that’s not allowed by our SOP” to prevent misuse.
- Data retention: codify that “All video recorded by drones will be stored on the secure server and retained for XX days, consistent with CCTV policy, then purged unless flagged for an incident. No footage shall be exported or shared externally without approval of Security Director and Legal.” This ensures chain-of-custody and privacy.
- Liaison with authorities: note that if a serious incident occurs that may involve law enforcement, the SOP is to preserve the footage and share with law enforcement as required. Possibly have a step to consult legal if any privacy concerns.
- Integration with Security Protocols: Modify existing security procedures to include drones:
- Alarm response SOP: When an alarm triggers, add a step “deploy drone if appropriate” after or in tandem with dispatching guard. For example: “If perimeter alarm triggers at sectors covered by drone patrol, SOC will immediately task the on-duty drone pilot to investigate via UAV, while also sending nearest guard.” Be specific for different alarm types (e.g., panic alarm vs motion alarm might have different handling).
- Incident command: If there’s an emergency (like a fire or active threat), define the drone pilot’s role in the incident command structure. Perhaps they report to the incident commander or feed them intel. Ensure the pilot doesn’t freelance outside the command structure in critical incidents.
- Daily routine: incorporate drone launch into shift checklists. Example: During night shift change, the departing supervisor will brief the incoming on drone status (any issues from last flight) and the incoming will do a test flight at shift start, etc. Or “At 9pm each night, a drone perimeter patrol will be conducted and its findings logged.”
- Coordination with guards: e.g., if ground patrols are scheduled, maybe have drones patrol other areas or provide overwatch. Write it such that they complement each other, not both doing same thing redundantly. Possibly schedule joint exercises so it’s routine.
- Regulatory Compliance SOP: Many of these items we’ve discussed, but it can help to have an SOP that specifically ensures FAA and legal compliance each flight:
- Always carry pilot certificate and drone registration on person (a Part 107 requirement if asked by authorities).
- How to handle any FAA or law enforcement inquiry (e.g., if police approach and ask about your flight, pilots should know to politely show credentials and inform them it’s an authorized corporate security operation, etc.).
- Remote ID: confirm it’s broadcasting (some systems allow checking via an app).
- Night operations: ensure strobe lights are on at civil twilight, etc.
- If any incident (crash, injury, property damage beyond threshold) occurs, SOP to notify management and file FAA incident report within 10 days as required (Drone Industry Visionary Interview: Ryan Smith defines the tangible (and invisible) ROI of drone security | Commercial UAV News) (Drone Industry Visionary Interview: Ryan Smith defines the tangible (and invisible) ROI of drone security | Commercial UAV News).
- Pre-filing of NOTAMs if applicable (rarely needed now with LAANC, but for a special event it might be considered).
- Observer usage if VLOS can’t be maintained, etc. – basically restating any waivers or conditions you must adhere to. If you got a waiver (say for over-people with a parachute system), the waiver conditions must be in SOP as mandatory steps.
- Maintenance SOP: If you have a maintenance schedule (say, every Monday check all drones’ propellers, or every 3 months replace batteries or send for professional tune-up), include that. Perhaps designate one pilot or technician as maintenance lead who ensures these tasks happen.
- Continual Training and Drill SOP: Indicate that pilots must conduct at least X hours of flight training per month to maintain proficiency (aside from operational flights). Or require periodic re-evaluation (maybe an annual internal test). Also plan periodic emergency drills (like simulate a drone flyaway or crash scenario and practice responding). These keep the team sharp and SOPs relevant.
Document all these SOPs in a manual or digital document repository. Have them reviewed by stakeholders (security management, legal, HR if needed, IT for any technical steps). Then finalize and disseminate to all involved personnel. Conduct a briefing or workshop on the SOPs to ensure understanding. Also, keep SOPs as living documents – note that after the pilot phase (next step) you will likely update them with lessons learned.
Step 4: Pilot Deployment and Evaluation
Before rolling out full-scale, it’s wise to conduct a pilot deployment – a limited, controlled introduction of drones to test your procedures, team, and technology in real operating conditions:
- Scope the Pilot: Determine which site or scenario to start with. Often it’s a single facility (perhaps your largest campus or conversely a smaller site to test on a manageable scale). Define duration – for example, a 60-day pilot program. During this period, you’ll closely monitor performance and make adjustments. Clearly state pilot objectives: e.g., “Validate that drone can reduce average response time to perimeter alarms by 50%” or “Ensure safe integration of drone patrols into nightly security routine without incident.”
- Gradual Introduction: In the first days of the pilot, operate the drone under ideal, low-risk conditions (maybe daylight, minimal activity on site) to ensure all systems work as expected. Then gradually extend to nighttime or busier times. This phased approach builds operator confidence and lets you catch any issues (like perhaps the IR camera has glare under certain lighting – you might need a filter or setting tweak).
- Real-World Testing: Use the drone in as many real scenarios as feasible:
- Perform routine patrols per SOP and see if any adjustments are needed (maybe you discover a certain waypoint has poor radio reception, requiring moving the home position or adding a signal booster).
- Trigger some test alarms (have someone intentionally set off a fence sensor or simulate an intruder) to gauge drone response. Time how long it takes from alarm to eyes on target via drone, and compare to past guard-only responses. This will give hard data on efficacy (e.g., drone arrived on scene in 90 seconds versus a guard’s 5 minutes). (Cost-Effective Security: Comparing Drone Security to Traditional Methods) (Cost-Effective Security: Comparing Drone Security to Traditional Methods)
- If possible, involve local law enforcement or first responders in a drill (especially if one objective is to feed them intel during an emergency). For instance, do a drill where the fire department responds to a mock accident in a remote part of campus and see how the drone can provide overhead views. Gather their feedback too – this can strengthen your program and relationship with them.
- Evaluate the team’s workload: Are pilots able to handle drone tasks along with other duties? Do you notice any bottlenecks like the pilot getting too many simultaneous requests? This will inform whether you need more personnel or a scheduling change.
- Collect Data and Feedback: Throughout the pilot, maintain a log of:
- All flights (from your flight logbooks).
- All incidents or anomalies (e.g., “8/12: Lost GPS lock for 10 seconds near building A – possibly due to interference from HVAC unit”).
- Security events detected or deterred by the drone (e.g., “8/15: Detected two unauthorized individuals at east fence – drone presence caused them to flee, guards confirmed no breach”).
- Any safety issues or near-misses (hopefully none, but record things like “battery low warning came earlier than expected, landed with only 5% – will adjust battery swap procedure”).
- Feedback from the security team at large: Are ground officers using the drone feed effectively? Do they find it helpful? Did anyone note concerns (like noise or distraction)? Possibly do a quick survey or debrief meetings.
- If using any analytics (like counting how often drone sees movement vs false alarms), note those outcomes.
- Evaluate privacy/ethical adherence: Did any situation raise a question (maybe the drone camera inadvertently caught a view into an executive’s office window – if so, note it and consider adjusting altitude or angle SOP to prevent that).
- Mid-Pilot Adjustments: Be flexible – if something is not working as intended, adjust on the fly. SOPs can be tweaked during the pilot. For example, you might find that doing patrols exactly on the hour is too predictable (if someone were studying your patterns), so you adjust to random interval patrols. Or you find the drone’s spotlight is very bright and shining into windows, so you adjust procedure to use it only when necessary rather than every patrol. Small course corrections like these are the purpose of the pilot phase.
- Measure Against KPIs: Refer back to the success criteria defined in planning. Collect metrics:
- Average response time to alarms before and during pilot.
- Number of incidents observed/detected by drone that would have been missed by regular means.
- Reduction in false alarm responses (perhaps drone verifies false alarms so guards didn’t have to roll out needlessly).
- Operational uptime of the drone (percentage of time it was available when needed vs down for charging or issues).
- Any cost savings realized in this short term (like less guard patrol overtime).
- End-of-Pilot Review: At the conclusion of the pilot period, convene all stakeholders (security management, drone team, IT, maybe an executive sponsor) to review results. Provide a report with the collected data and anecdotes. Highlight successes: e.g., “No safety incidents occurred; drone responded to 5 alarms with an average 3-minute faster visual confirmation; detected 2 security issues proactively.” Also be candid about challenges: “We experienced intermittent video dropouts around Warehouse 4 – likely due to Wi-Fi interference; recommend installing an extender or adjusting flight path.” Present solutions to each challenge.
- SOP Refinement: Based on pilot learnings, update the SOPs and policies. Perhaps you realized you need an additional pre-flight check (like verifying the SD card is inserted – if someone forgot during pilot and lost a recording opportunity, add it to checklist). Or maybe the team found a better way to coordinate with guards, so rewrite that section. These refinements will be implemented in the full rollout.
- Go/No-Go Decision for Expansion: Ideally, the pilot confirms viability and you proceed. If significant issues arose, you might extend the pilot or do a second pilot after adjustments. Assuming success, document the green light to expand – likely the executive champion will want a briefing or report. Provide them the results and the plan for scaling up (which is next step). Perhaps include any budget adjustments needed (maybe more batteries or an extra drone if pilot showed heavy usage).
- Communicate Results to Staff: If you previously informed employees about the pilot, close the loop. For instance, send a brief note, “Our test of drone security patrols over the last two months was successful – it helped improve our response and no privacy concerns were reported. We plan to fully implement this technology next quarter. Thank you for your cooperation.” This maintains transparency and acceptance.
The pilot phase is about learning and building confidence. By the end, your team should feel fully ready to handle drones as part of daily operations, and you’ll have ironed out initial wrinkles. It’s much better to discover and fix these in a trial run than after full deployment.
Step 5: Full Deployment, Scaling, and Continuous Improvement
After a successful pilot, you’re ready to roll out the drone program fully across the intended scope. This step focuses on scaling operations, integrating drones as a permanent part of security, and establishing feedback loops for continual improvement.
- Rollout Plan: If the program will cover multiple sites or an entire campus beyond the pilot area, create a phased rollout schedule. For example, “Month 1: extend drone coverage to all perimeter sectors. Month 2: introduce second drone for overlapping coverage or daytime patrols. Month 3: include drones at secondary facility across town,” etc. Staggering helps manage training and resource load. Ensure each new addition gets a mini-pilot of its own (maybe shorter since lessons are learned – but still, test at each site).
- Resource Scaling: Procure additional equipment as needed based on pilot findings:
- If pilot showed one drone handled nights well, but you want coverage 24/7, you may need a second unit for daytime or as backup. Acquire that now. Always have at least one backup drone in case the primary goes down for maintenance or repair.
- Buy spare parts and extra batteries identified during pilot (if you realized you needed more batteries to maintain continuous coverage, ensure those are purchased).
- Expand infrastructure: maybe set up multiple drone base stations (launch/landing pads) around the property for efficiency. Some large facilities designate a few safe landing zones so the drone can auto-land nearest to an incident if battery is low, etc. If you opt for a drone-in-a-box solution for autonomy and weather protection, install those units now at strategic locations.
- Ensure redundancy in personnel: train a couple more pilots or observers if needed so you’re covered across all shifts, including vacations or turnover. You might create a formal “UAS unit” within the security team with a lead and multiple operators.
- Integration into Routine: Normalize the drone operations as just another component of security:
- Incorporate drone status into shift briefings. E.g., during every guard mount/roll-call, mention drone assignments: “Drone patrol will cover Sectors 1-3 this shift, pilot is Officer Jones. All officers, coordinate as needed.”
- Add drone feed monitoring to SOC routine. If you have a video wall, maybe dedicate one screen to the drone when it’s up, or ensure the SOC knows how to quickly pull it up on demand. Over time, operators will instinctively check the drone camera along with fixed cameras when something’s up.
- Use the drone proactively: not just for alarms, but encourage the team to leverage it whenever it could help. For instance, if an employee calls reporting a suspicious person in parking lot D, the SOC can dispatch the drone immediately to surveil, even if no formal alarm was triggered. The more use-cases you fulfill, the more value it provides.
- However, also avoid overusing it for trivial things so that maintenance and resources aren’t wasted (balance is key).
- Ongoing Training and Proficiency: Schedule regular training drills and recertifications:
- Perhaps quarterly scenario drills where the drone team and ground team practice a particular situation (intruder scenario, lost child scenario, etc.). This keeps skills sharp and identifies any new improvement points.
- Keep pilots updated on any new drone firmware or capabilities and train them on those. Tech evolves – for example, if a new software update enables better tracking or new flight modes, incorporate that after testing.
- Cross-train additional team members (maybe new hires or others who express interest) to build a pipeline of qualified operators. This also fosters resilience if a key pilot leaves.
- Encourage your drone team to attend security industry events or read up on latest best practices (ASIS webinars on drones, etc.), to continually infuse new ideas.
- Maintenance and Lifecycle Management: Now that drones are live, treat them like fleet vehicles or other equipment:
- Perform maintenance per schedule religiously (battery replacements after X cycles, motor servicing, calibration checks, etc.). Keep a maintenance log separate from flight log.
- Monitor the “health metrics” – many enterprise drones provide data on battery health, motor output, internal temperatures, etc. Review those logs monthly to predict if a component might fail. Early detection of wear can prevent an incident.
- Plan for eventual upgrades or expansion. Typically, drone hardware might be very effective for 2-3 years, but you should stay aware of improvements. You don’t need to chase every new model, but have a tech refresh plan in say 3-5 years to take advantage of longer flight times or better sensors that come out (especially if your program grows – e.g., in a few years you might want to deploy multiple smaller autonomous drones, or add a fixed-wing for long-range if BVLOS becomes easier).
- Budget annually for maintenance costs (new batteries, propellers, maybe manufacturer support contracts). These should be part of security OPEX now.
- Policy Enforcement and Updates: Ensure that all the policies (privacy, safety, etc.) are being followed as drones become routine. Conduct periodic audits:
- Review random video clips to ensure nothing inappropriate is being recorded or that operators didn’t inadvertently stray into a no-fly zone.
- Check flight logs against SOP – were pre-flight checklists completed? If not, retrain or enforce.
- Solicit feedback from employees or neighbors periodically: any complaints about noise or privacy? Address them promptly. E.g., if someone says the drone’s night strobe is shining into their home outside the fence, maybe adjust altitude or direction in that sector.
- Update policies if regulations change (e.g., if FAA loosens some rule or adds a new one like Remote ID – which we addressed – make sure SOPs evolve accordingly). Also update if your company’s broader policies (like privacy policy) evolve.
- Metrics and Continuous Improvement: Now that drones are a steady part of operations, track key performance indicators (KPIs) over the long term and look for trends:
- Incident rates in areas under drone surveillance – did they drop compared to before? If yes, great – showcase that to maintain executive support. If not, why? Are perpetrators not deterred by drones, or are they shifting tactics? Use that intel to adapt – maybe they now hide from the drone, so you adjust patrol timing or add a second drone to outsmart them.
- Response times – are you meeting the targets you set (e.g., getting eyes on an alarm within 2 minutes)? If creeping up, figure out why (too many simultaneous tasks for one drone? Battery swaps causing delay? Solve by adding a second drone on staggered schedule or improving battery capacity, etc.).
- Cost savings – at year-end, calculate approximate savings or cost avoidance. E.g., “We reduced on-foot patrol hours by 20% due to drone supplementation, saving $X. We prevented 3 major thefts (worth $Y) that likely would have succeeded previously.” These metrics not only prove ROI but guide resource allocation (maybe you can justify adding another drone or retaining the program in budget cuts).
- Safety record – track any incidents or absence of them. “Zero drone-related injuries or crashes this year” is a point of pride and justification for the program’s professionalism.
- Use these metrics to refine the program. If one metric is lagging (say false alarms are still frequent), maybe the solution is to integrate an AI analytics system on the drone feed to filter out, or adjust sensors – continual improvement mindset.
- Consider conducting a formal Program Review annually, involving cross-department stakeholders (security, HR, legal, IT). Review the data, any incidents, compliance status, and emerging needs. For instance, maybe now other departments have interest (Facilities might want to use drones for roof inspections; you could branch out in a controlled way). Or maybe new threats emerged that drones could help with (like increased protest activity at corporate HQ – so maybe implement a crowd monitoring SOP via drone).
- Documentation and Knowledge Management: Keep all documentation up to date:
- Revise the Drone Operations Manual (SOP document) whenever changes are made, and redistribute to the team.
- Maintain a training log of all operators (dates they were trained, certified, any refreshers).
- Document any incidents with analysis (essentially a lessons-learned library). If something odd happened and was resolved, write it down so new pilots can be warned (“Heads up: around Building 5 the GPS can glitch due to the steel structure; be ready to switch to manual there.”)
- Have an easily accessible repository for drone footage related to past incidents that can be used for training or evidence if similar incidents occur again (with proper access controls).
- Celebrate and Communicate Success: When the program is fully implemented, recognize the team and share successes with higher-ups and potentially the whole company. For example, publish an internal article: “Our new drone security system helped prevent a costly break-in last quarter – thanks to the Security team’s innovation.” This not only boosts morale but also reinforces the program’s value, making it less likely to be cut if budgets tighten.
- Stay Adaptive: The security landscape and technology landscape will evolve. Keep an eye on:
- Emerging drone tech: as covered in the next section (Future trends), things like AI, swarms, counter-drone systems. You don’t need to adopt everything, but being aware means you can plan upgrades. For example, if FAA allows routine BVLOS in 2 years and you have multiple sites to cover, you could consolidate drone ops centrally – but that needs planning and new SOPs.
- Threat evolution: If criminals find ways to evade drones (maybe using disguises or trying to shoot them down or hack them), be prepared with countermeasures (maybe incorporate counter-drone detection to protect your drone or coordinate with law enforcement on such events).
- Regulation changes: Stay compliant as laws shift. Perhaps new privacy laws might directly address corporate drone use in the future – be ready to adapt policies.
- Business changes: If your company expands to new locations or has new assets, consider whether to extend the drone program there. Conversely, if a facility closes or risk profile drops, you might reassign drones elsewhere.
By following through these implementation steps, your drone surveillance program becomes an integral, reliable component of corporate security. It should not be seen as a “project” anymore, but as an ongoing operation within the security department, with allocated budget, personnel, and strategy. The key to long-term success will be staying proactive: continually training, monitoring results, and improving processes. In doing so, you ensure the program keeps delivering strong security outcomes and justifying its place in the corporate security strategy.
Strong Call-to-Action (CTA):
Ready to elevate your organization’s security and resilience through advanced drone surveillance? Partner with Cuneo Consulting—trusted experts in physical security, offering specialized consultations, comprehensive program audits, and fully managed drone surveillance services. Ensure your security strategy is future-ready and professionally managed by industry specialists.
The Future of Drone Surveillance: Emerging Technologies and Trends
Having established a robust drone surveillance program today, it’s important to look ahead at how technology and regulatory trends will shape the future of drone use in corporate security. This final substantive section explores emerging developments that could further enhance (or challenge) your program in the coming years. We’ll discuss advancements in artificial intelligence (AI) and automation that are making drones smarter and more autonomous, the concept of drone swarms for covering large areas collaboratively, and improvements in battery and propulsion technology that could extend flight times or enable new types of drones (like fixed-wing or hybrid VTOL for longer range). We’ll also examine evolving regulations – for instance, progress toward routine BVLOS operations as aviation authorities and industry push the envelope – which could allow a single pilot or command center to oversee drones that patrol vast distances or multiple facilities from afar. Additionally, we address the rise of counter-drone concerns and tools: as beneficial as drones are for security, they can also be a threat if used by bad actors, so we’ll look at how corporate security might need to detect and mitigate unwanted drones (and how regulatory changes are enabling that).
For executives planning strategically, we’ll highlight how to future-proof your investments: choosing systems that are modular or upgradable, staying agile with training in new skills (like AI operation), and keeping an eye on standards (such as Remote ID and potential UTM – Unmanned Traffic Management – systems that could integrate with your security drones). We also note industry trends like “Drone-as-a-Service” models, where companies may outsource drone flights to specialized service providers – a trend that might influence budgeting and staffing. The goal here is to provide insight so that your corporate security leadership can anticipate changes and position the drone program to take advantage of new tech while mitigating new risks.
By understanding what’s on the horizon – from AI analytics that can identify a trespasser automatically, to drone docks enabling 24/7 autonomous patrols, to swarm response for large-scale incidents – you can ensure your security strategy remains cutting-edge and effective in the years to come.
AI and Automation: Smarter Eyes in the Sky
One of the most transformative trends in drone technology is the integration of artificial intelligence (AI) and advanced automation. This has direct implications for corporate security:
- Automated Threat Detection: Today, a human pilot or security operator typically watches the drone feed to spot intruders or anomalies. AI video analytics, however, are becoming capable of doing this in real-time. Just as modern CCTV systems can employ AI to detect a person or vehicle and alert operators, drones can stream their video through AI algorithms that identify security events automatically. For example, an AI could be trained to distinguish between authorized personnel and someone not in uniform in a restricted area, or to detect a person climbing a fence at night (differentiating them from, say, a deer triggering a motion sensor). According to a Security Industry Association report, AI and machine learning are rapidly transforming surveillance analytics, enabling predictive threat detection (Navigating Modern Security Challenges: The Crucial Role of Physical and Surveillance Security Solutions – Cuneo Consulting). In practice, this means your drone could send an alert – “Intruder detected by thermal camera in Zone 3” – without the operator having to notice it manually, effectively acting as a smart guard. As these algorithms get more sophisticated, they’ll reduce false alarms by learning normal patterns (like employees leaving at scheduled times) and flagging only the unusual.
- Autonomous Patrols and Response: While you may already have semi-autonomous waypoint missions, the future is drones that can decide when and where to patrol based on live data and cues. Using AI, a drone might dynamically adjust its patrol route if, for instance, it “predicts” higher risk in a certain area (perhaps there was motion detected on a fence sensor – the drone can self-direct to scan that area more frequently). AI could also help optimize coverage: multiple drones could coordinate to ensure the entire property is surveilled efficiently without gaps, handing off areas between them intelligently. We are moving toward an era where you could tell a drone network “keep the site secure” and it figures out the rest, with minimal human intervention.
- Object Recognition and Tracking: Beyond just detecting humans, AI can recognize specific objects or behaviors. For security, this could mean identifying a weapon in someone’s hand from the air, or recognizing a particular vehicle license plate and tracking that vehicle across the campus. Imagine a scenario where an unauthorized drone (a spy drone) flies onto your property – future AI-enabled security drones could detect the intruding drone (by visual or RF signature) and even autonomously track or interdict it (more on counter-drone later). Some drones already have AI-based tracking that locks onto a person or vehicle and follows them. As this becomes more robust, one pilot might supervise while the drone auto-follows a suspect through complex terrain, freeing the pilot to coordinate ground responders.
- Reduced Workload via Machine Learning: AI might also streamline post-incident work by automatically reviewing hours of footage and flagging the relevant parts. For example, if an incident happened overnight, an AI system could quickly search the entire night’s drone video for motion at that specific area and time, saving analysts a lot of time. Machine learning models could even correlate drone sensor data with other inputs (like alarms, access logs) to provide comprehensive incident reports. This trend points to security personnel shifting to more of a management and decision role, as AI handles the mundane watching and initial analysis.
- Natural Language and Voice Command Interfaces: It’s plausible that controlling drones will become easier through AI-driven interfaces. In the future, a security operator might say or type into the system: “Drone, check Parking Lot C for any loitering individuals,” and the AI will interpret that and dispatch a drone to do it, using onboard analytics to fulfill the request and then respond, “Parking Lot C is clear.” This reduces the need for highly technical piloting skills for every action, broadening who can task drones (perhaps a shift supervisor could verbally request drone assistance while still focusing on other duties).
- Predictive Patrols: With enough data over time, AI might start predicting when and where incidents are likely to occur (much like predictive policing algorithms). For example, learning that past trespassing attempts often happen on rainy weekends at a certain corner of the property, the system might suggest (or automatically schedule) extra drone patrols during those conditions. This is similar to how some systems predict where crimes might happen (Navigating Modern Security Challenges: The Crucial Role of Physical and Surveillance Security Solutions – Cuneo Consulting) – integrating that insight with drone scheduling could pre-empt incidents.
For executives, the takeaway is that AI will make drones more proactive and less reliant on constant human control. This can improve security efficacy but also means investing in the right software and talent. You might need data scientists or security analysts who understand and trust AI outputs. It also raises new questions: how to avoid AI biases or errors (e.g., an AI might misidentify a harmless situation as a threat – you’ll need procedures to verify AI alerts). But overall, incorporating AI could let you scale your security coverage without equivalent scaling of personnel.
One should keep an eye on industry developments and consider AI-ready platforms. Many enterprise drone systems are already offering AI add-ons or cloud analytics. For example, some drones have APIs to stream video to third-party AI services (like Amazon Rekognition or specialized security AI software). In planning upgrades, design your infrastructure to accommodate these (ensuring you have bandwidth and compute either on-premise or via cloud to handle the heavy processing of AI).
Bottom line: In the near future, expect your “unblinking eye” in the sky to also become a “thinking eye,” helping your team work smarter, not just harder. Embracing AI safely and effectively will be a key differentiator in advanced corporate security strategy.
Drone Swarms and Multi-Domain Integration
Today, we usually operate drones one at a time, but tomorrow’s paradigm could be drone swarms – multiple drones working in concert under a single control framework. For corporate security, swarm capabilities could offer game-changing coverage and redundancy:
- Coordinated Coverage: Imagine a large industrial campus where instead of one drone doing a big loop, you have 3–5 smaller drones that take off simultaneously and each covers a sector, sharing data. They could communicate with each other to ensure one picks up where another left off. This drastically cuts down the time to surveil a large area. If an intruder is detected moving across the facility, one drone can track the target while others reposition ahead of the person to box them in or continue monitoring if the target changes direction. Essentially, a swarm acts like a net of eyes, much harder for an intruder to evade.
- Autonomous Coordination: In a true swarm, drones are aware of each other and collaborate without constant human micromanagement. If Drone A’s battery is low, Drone B could automatically cover its zone until A is back from charging. Or if an intruder is detected, the nearest drone engages in tracking while neighboring drones autonomously create an expanding perimeter search to check for accomplices or diversion tactics. All this could be managed by an AI “hive mind” that assigns roles to each drone on the fly.
- Different Drone Types in Swarm: A future scenario might mix drone types for multi-domain awareness. For example, a fixed-wing drone could provide high-altitude wide-area surveillance (like a persistent watch at 400 ft seeing the whole campus), while several quadcopters serve as rapid responders that zoom in when the fixed-wing spots something. The fixed-wing could relay coordinates to the rotaries, which then handle close inspection. This multi-layered approach plays to each platform’s strength. The U.S. military is experimenting with such concepts, and trickle-down to corporate security could happen, especially for very large facilities (think utility companies with miles of pipeline or rail companies along tracks).
- Swarm Economics: As drone hardware costs potentially decrease and software gets smarter, deploying multiple drones might become cost-effective. Instead of one $20k drone, you might have five $5k drones that together cover more area faster and provide redundancy. If one fails, the others fill in – improving reliability of coverage (no single point of failure). Executives should watch this space because a swarm could potentially reduce the need for multiple expensive high-end drones – a network of simpler drones could do the job and be more resilient. Some companies are already showcasing “drone-in-a-box” systems where multiple small drones live in charging hubs around a property and launch as a team on schedule or on-demand.
- Regulatory Movement: Currently, regulations like Part 107 require one pilot per drone, which limits swarm use unless you get waivers. But regulatory bodies are actively researching unmanned Traffic Management (UTM) and swarming concepts. The FAA’s UAS BEYOND program and others are looking at how one operator could oversee many drones (with automation). We can anticipate that in 5–10 years, regulations will adapt to allow certain trusted autonomous swarm operations, especially in controlled airspace or private properties with risk mitigations. Already, beyond visual line of sight waivers sometimes allow supervising multiple craft via tech.
- Use Cases for Swarms in Security: Beyond intruder tracking, swarms could be useful for event security. Picture a large corporate event or open-air conference: a swarm of mini-drones could blanket the area providing overhead views of crowd flow, detecting any disturbances or medical emergencies faster than ground spotters. They could also be used for search and rescue on company grounds – say an employee is lost in a vast mining site at night, a swarm of drones can search different grid segments rapidly (some equipped with thermal, others with spotlight, etc.).
- Integration with Other Robotics: We should also consider the future where drones coordinate with ground security robots or fixed sensors. For example, if a ground robot encounters a situation it can’t see over (like a tall fence or a building corner), it could signal a drone to come get an overhead look. Or fixed thermal cameras on poles detect movement and cue a swarm launch to that location. This is the notion of multi-domain integration: aerial, ground, and even marine robots (if relevant) sharing a common operating picture. Tech giants and security integrators are indeed pushing for unified platforms controlling cameras, drones, access control, and robots under one AI-driven command center (Navigating Modern Security Challenges: The Crucial Role of Physical and Surveillance Security Solutions – Cuneo Consulting). This holistic approach could vastly improve situational awareness and response coordination – the drone is one asset among many, all linked.
Preparing for swarms means building the modular infrastructure and open systems now. Choose drone systems that are swarm-capable or at least swarm-ready (some enterprise drones can be upgraded to multi-drone coordination via software updates or add-ons). It also means adjusting SOPs: with multiple drones airborne, you’ll need more sophisticated airspace de-confliction and automation – which likely implies relying on AI/automation to manage that because a human juggling five drone control sticks is impractical. So, adopting swarms goes hand-in-hand with adopting AI as discussed.
Executives should keep an eye on the legal environment: eventually regulations will likely allow one operator to manage a fleet of autonomous security drones with appropriate safety systems (remote ID, reliable communications, automated detect-and-avoid for collisions, etc.). When that happens, security operations could scale dramatically without equivalent staff increases.
Action item for future-proofing: If your vendor or security partner offers a roadmap that includes multi-UAV management or swarm features, consider participating in early trials. It could give your organization a competitive edge in security readiness. Additionally, start developing protocols for how multiple drones would be used in your context – even if you only have one now, a written concept of operations for two or three can prepare you for quick adoption later.
Beyond Visual Line of Sight (BVLOS) and Remote Operations
One of the current limitations on drone operations is the requirement to keep drones within the operator’s Visual Line of Sight (VLOS). However, efforts are underway to safely enable Beyond Visual Line of Sight (BVLOS) flights, which would be a game-changer for corporate security:
- Extended Range Coverage: With BVLOS approval, a single drone (or a few) could cover far larger areas or even multiple sites from one central location. For instance, a security operations center in one city could oversee drones patrolling several facilities across a region, each drone launching from its home site but controlled over cellular or satellite links by the remote team. For companies with dispersed assets (like utility lines, pipelines, remote campuses), this could dramatically improve efficiency. Titan Aviation got a nationwide BVLOS waiver to operate security drones remotely (Drone Industry Visionary Interview: Ryan Smith defines the tangible (and invisible) ROI of drone security | Commercial UAV News), which demonstrates how industry is moving this way.
- Economies of Scale: BVLOS could reduce the need to have a certified pilot at each site. Instead, you might have a central pool of pilots or even largely autonomous ops with a smaller oversight team. This centralization is attractive for cost and consistency – all sites get the same level of advanced drone surveillance without each needing a full drone staff. Executives should envision whether in the future they want to manage a “drone security hub” that provides aerial security services to all company locations (like an internal drone security service bureau).
- Persistent Surveillance: BVLOS enables using drones as long-endurance sentries. For example, a fixed-wing drone could fly a perimeter continuously for hours beyond sight of any operator, as long as there’s a communication link. It could be programmed to only alert home base when it sees something. Essentially, drones become flying CCTV cameras on endless patrol. Some startups are already offering semi-BVLOS solutions on private land (with waivers), where drones fly pre-set routes around, say, large solar farms miles long. As regulators become more comfortable (likely aided by technologies like detect-and-avoid sensors, reliable command links, and the implementation of the Remote ID system to keep the airspace organized), we can expect more routine BVLOS allowances for low-risk environments like private security over private property.
- Regulatory Momentum: Regulatory bodies internationally are testing BVLOS. In the US, the FAA’s BEYOND program is working on standards for routine BVLOS. They have hinted at proposing new BVLOS rules possibly in the mid-2020s. This might include requirements like using specific radar or optical observers, or limiting BVLOS to rural/controlled areas. For corporate campuses, especially those in less populated areas, it’s likely to become feasible to get permissions to operate BVLOS with minimal extra tech if one can show the operation is low-risk (e.g., below a certain altitude, away from airports, with certain safety mitigations). When that happens, corporate security drones could conceivably roam an entire city’s worth of facilities from one base.
- Teleoperations: Hand-in-hand with BVLOS is the idea of remote drone operations – controlling drones over the internet or private networks. Companies like American Tower (cell towers) and some security firms are already trialing remote operations centers where an operator sees the drone’s view via streaming video and controls it like a video game from hundreds of miles away. For security, this means you might outsource or consolidate pilot duties. Perhaps your security integrator or a specialized service runs your drones for you from their control room, calling on you only when needed on the ground. This Drone-as-a-Service model is emerging. If your company prefers not to maintain an internal drone team long-term, you might eventually opt for such services once regulations allow one control center to handle many clients’ drones safely.
- Satellite and 5G Connectivity: BVLOS is heavily enabled by robust connectivity. The rollout of 5G networks with network slicing for drones, and low-earth orbit satellite internet (Starlink, etc.), means even remote facilities could have drones connected to high-speed networks. That is crucial for remote control and high-quality video backhaul. As your company upgrades its networks or works with telecoms, consider connectivity for drones as a requirement (e.g., ensuring good 5G coverage over plant sites, or installing private LTE/5G networks on large campuses – these can carry drone data securely).
- New Use Cases Unlocked: When you can fly BVLOS, you might discover new security tasks:
- Inter-facility response: If an alarm triggers at a facility with no on-site security, a drone from a nearby site could fly over to have eyes until local authorities arrive.
- Supply chain security: A drone could escort high-value shipments between facilities, e.g., following a truck for dozens of miles (some companies have tested drones launching from truck roofs to extend the truck’s situational awareness).
- Emergency logistics: In a crisis, a security drone BVLOS could even ferry a small item (like an access card or first aid kit) to a location, functioning as part of emergency response beyond just camera usage.
To prepare for BVLOS opportunities, businesses should:
- Start integrating redundant controls and sensors that might be needed (for instance, consider drones with ADS-B in/out to be aware of other aircraft – often a requirement for BVLOS near air traffic).
- Work on SOPs for lost link and other contingencies in extended operations (because the drone might be far when something goes awry, so it needs robust automated return or holding patterns).
- Possibly engage in pilot programs or waivers now if BVLOS would significantly improve your security coverage. Being an early adopter can give you operational experience and influence on shaping best practices.
Executives should monitor regulatory updates from FAA, EASA, etc., and be ready to adjust policies. Also, engaging with industry bodies (e.g., joining a drone advisory committee or working group via your security associations) can give insight and a voice in how these rules develop.
In summary, BVLOS will largely erase geographical constraints on your drone surveillance capabilities. It moves the concept from “a drone per property” to “a network of drones for the company, managed wherever.” That future can elevate corporate security to a new level of responsiveness and integration, essentially creating a private aerial security network akin to how we use CCTV networks now, but with far greater reach.
Counter-Drone Measures: Protecting Against Unwanted Eyes in the Sky
As drones become more integral to security, they also become tools that adversaries might exploit. Corporate espionage, protest groups, or vandals could deploy their own drones to surveil or disrupt your operations. Thus, counter-drone (C-UAS) strategies will likely become a necessary part of modern corporate security. Here’s what to consider:
- Threat of Rogue Drones: An uncrewed aerial intruder could gather intelligence by filming your campus, attempt to violate privacy of execs (paparazzi drones are a thing), or even carry malicious payloads. There have been cases of drones dropping propaganda leaflets, or potential to drop incendiary devices, etc. Even retail thieves might use drones to scout for weak entry points or see if security patrols are active (a sort of reverse surveillance on your security).
- Drone Detection Systems: The first step in countering rogue drones is knowing they’re there. Specialized systems use RF scanners, radar, and optical/thermal cameras to detect and track drones in your vicinity. For example, RF analyzers can pick up the communication signals between a drone and its controller (many drones use common frequencies), alerting you that a drone is nearby (The Rise of Drones and Counter-Drone: A Double-Edged Sword in the Skies) (The Rise of Drones and Counter-Drone: A Double-Edged Sword in the Skies). High-end solutions can even triangulate the position of the drone and the pilot’s controller (The Rise of Drones and Counter-Drone: A Double-Edged Sword in the Skies) (The Rise of Drones and Counter-Drone: A Double-Edged Sword in the Skies), which is hugely useful – it not only tells you “a drone is overhead at these GPS coordinates” but also “the operator is over there on that hill.” Radar can detect the physical presence of drones, even autonomous ones not emitting RF. Some cameras with AI can detect a drone in the sky visually if within line of sight. Many systems fuse these sensors to reduce false alarms (distinguish drones from birds, etc.). As a corporate security head, you might not deploy this day one, but if your risk assessment (or an incident) shows a threat from drones, investing in a detection system around key facilities is prudent.
- Interdiction and Mitigation: Once detected, how do you stop a malicious drone? This is tricky territory legally. In the US and many countries, shooting down or jamming a drone can violate laws (since drones are protected as aircraft and communications). Currently, only federal agencies (and in some cases specially designated state law enforcement) have authority to interdict drones (e.g., DOJ, DHS units can use drone jammers under certain laws). However, there are emerging solutions and evolving legal allowances:
- Jamming / RF Takeover: Systems exist that can jam the control frequencies or GPS of a drone, causing it to lose control (often triggering its fail-safe to land or return home). More sophisticated ones like RF cyber takeover actually hack into the drone’s link and commandeer it (The Rise of Drones and Counter-Drone: A Double-Edged Sword in the Skies) (The Rise of Drones and Counter-Drone: A Double-Edged Sword in the Skies). The ASIS article snippet describes how RF “cyber” systems can precisely take control without collateral interference (The Rise of Drones and Counter-Drone: A Double-Edged Sword in the Skies) (The Rise of Drones and Counter-Drone: A Double-Edged Sword in the Skies). These tools are typically restricted to government use right now, but it’s possible that critical infrastructure companies or high-risk corporations might get waivers or future legal provision to use them, especially as the threat grows. In any case, tech is there, so executives should know it’s not sci-fi: there are literally “drone catcher” devices.
- Drone vs Drone: Another mitigation is using interceptor drones. These are fast drones that chase the rogue and disable it, perhaps by deploying a net or simply colliding with it to knock it out of the sky (sacrificing themselves). Some startups market “drone hunter” UAVs that autonomously engage unauthorized drones. For a corporate campus near sensitive facilities, one could envision keeping an interceptor drone docked and ready. If detection system flags an intruder, the interceptor launches and neutralizes it. This raises safety concerns (falling objects), so nets or controlled captures are preferred to simply kamikaze hits.
- Geofencing and Cybersecurity: On the preventive side, ensure your own drones and data are secure (so they can’t be hijacked). Use drones that employ strong encryption on their links so outsiders can’t easily snoop or take control (most enterprise models do). Also, maintain updated firmware to patch vulnerabilities that hackers could exploit (Do Drone Users Care About Data Security – DRONELIFE). On geofencing – many drone makers allow programming no-fly zones into your drone’s software. Conversely, if a rogue drone is a common make, sometimes detection systems can force a geofence on them or exploit built-in restrictions (DJI, for instance, has geofencing that law enforcement can request to activate in emergency situations to ground all DJI drones in an area).
- Policy and Legal Response: Have a plan in your security SOP for drone sightings. For example, if a suspicious drone is spotted, what do your security officers do? Likely: track it visually, try to identify the operator (often they’ll be line-of-sight too, maybe in a nearby parking lot), and call law enforcement if there’s clear malicious intent. Document and video-record its activity – that footage can be evidence for charges under laws like trespass or peeping tom statutes. In some jurisdictions, if a drone flies low over private property in a harassing manner, the property owner might have some rights to counter it (these laws are evolving; e.g., a few years ago a man shot down a drone over his yard and it went to court – outcomes vary, but generally you can’t do that due to airspace rules).
- Lobbying for Authority: Industry groups including those in security are advocating for clearer laws to allow critical infrastructure and possibly corporations to use counter-UAS measures legally. Executives of companies that face high drone threats may consider joining these advocacy efforts or at least staying informed. For instance, as of now, if a drone is spying on your corporate R&D facility, your hands are somewhat tied legally – you rely on law enforcement. But if that becomes a common issue, companies will push lawmakers to let them deploy defenses. Keep your legal team in the loop on this and perhaps prepare a strategy (e.g., if you’re a power plant, maybe coordinate with DHS which under certain programs can protect your site with their equipment).
- Privacy and Public Perception: Using counter-drone tools on your property is sensitive. You must ensure any detection tech complies with privacy laws (e.g., RF sensors should not intercept communications beyond identifying the drone control signals – typically they don’t decode content, just detect presence). Also, blasting jammers can affect legitimate devices if not carefully targeted (most modern ones are very directional to minimize collateral interference). Should you deploy these, transparency and responsibility are key to avoid scaring employees or neighbors. Ironically, you don’t want to be seen as the “all-watching company that will shoot down your kid’s quadcopter if it strays over the fence.” So these measures should be proportional and mainly for serious threats.
Planning for counter-drone is essentially planning for the next evolution of perimeter security – not just keeping people out, but also uninvited drones. Many experts view this as the next big security challenge (The Security Implications of Drone Threats). As ASIS notes, clear guidelines must be established as systems become widespread (The Rise of Drones and Counter-Drone: A Double-Edged Sword in …).
Future Integration: We spoke about swarms and integration – likely, future security systems will merge drone detection with your overall security dashboard. So the same command center that sees a break-in will also show an alert “Unknown drone detected at north fence, 300 ft altitude moving west.” Your drone program might eventually need a “counter-drone SOP” alongside normal operations: e.g., how to respond – possibly launch one of your own drones to investigate the unknown one (a benign approach if jamming not allowed), or notify authorities, or trigger an acoustic deterrent (some systems emit sounds that disrupt drones).
To future-proof, consider adding at least drone detection capability to your security upgrade list. Even if you don’t mitigate directly, knowing if and when rogue drones are overhead is valuable intelligence (you can then cover windows, pause sensitive conversations, etc., if you know a camera might be snooping).
In sum, as you raise your security via drones, be aware adversaries might do the same. Plan a 360-degree security posture that includes looking at the skies not only with friendly eyes but also watching out for hostile ones.
( ASIS references: (The Security Implications of Drone Threats)
Future-Proofing Investments and Strategy
Given all these emerging trends – AI, swarms, BVLOS, counter-drones – how can corporate security leaders future-proof their drone surveillance program?
- Invest in Upgradeable Systems: When choosing hardware and software, favor platforms known for regular updates and modularity. For instance, some enterprise drones allow payload swapping; today you may use a visual + thermal camera, but in a couple years you might swap in a more advanced AI processing module or a better sensor without buying a whole new drone. Similarly, choose a software ecosystem that is extensible – one that can integrate new analytics or additional drones easily. Avoid very closed systems that might not play well with new tech (e.g., if a vendor doesn’t support adding third-party AI tools, you might be stuck). Emphasize open APIs and compatibility when talking to vendors.
- Scalable Infrastructure: Build your drone operations center with room to grow. If you anticipate maybe going from 1 to 5 drones, set up your data storage, network bandwidth, and monitoring screens with that in mind (it’s easier to over-provision a bit now than overhaul later). Use cloud services that can scale or a VMS that supports many channels so you’re not at a dead end after a certain number of video feeds. If you plan multi-site expansion, perhaps establish a cloud-based video archive so all drone footage from all sites goes to one place (with proper access controls per site management as needed). This also aids in centralized analysis.
- Continuous Training and Learning: Encourage your drone team to stay on top of industry developments. This could mean attending security conferences that increasingly feature drone/UAS tracks (like ASIS’s GSX or specialized UAS security summits). Perhaps budget for advanced training in AI or new equipment when those become relevant. Some team members might get specialized in counter-drone tech, for example. Create a culture that adapts – maybe have quarterly brainstorm meetings on “new tech in security” where the team discusses how things like AI or 5G or new regs could be leveraged or need addressing. This keeps the program dynamic rather than static.
- Vendor Partnerships and Trials: It might be wise to maintain relationships with drone technology vendors beyond just buying things. Sign up for pilot programs or beta tests if offered – for example, some companies pilot-tested Remote ID modules early or new AI analytics. By partnering, you get early access (advantage over potential threats who might not have that) and you can shape the features to your needs. Likewise, be in contact with your integrators or consultants (like Cuneo Consulting) about what they see in the pipeline. If, say, a swarm management software is hitting the market, you might volunteer a site to test multi-drone patrols.
- Budgeting for Growth: Make sure your long-term security budget acknowledges that drones (and possibly counter-drone) will be an evolving line item. You may save costs in some areas (fewer guards or less theft), but you want funds available to upgrade drones every few years or to add an AI module subscription, etc. It’s easier to justify these incremental improvements if you’ve been tracking ROI and incident reduction. Essentially, reinvest some of the “savings” drones create back into the program to keep its edge. For example, maybe set a plan to replace one-third of your drone fleet every 3 years with newer models, cycling the oldest out – that prevents an obsolete fleet.
- Policy and Legal Monitoring: Keep your legal team or a compliance manager tasked with monitoring changes in drone law (FAA reauthorization acts, state laws on surveillance, etc.). For example, if a law comes that allows private entities to use certain counter-drone jammers with a license, you want to jump on that if you have a need. Conversely, if privacy laws tighten (like requiring additional notice to employees for aerial recording), you’ll need to adjust your practices quickly to stay compliant. Being proactive here avoids scrambling later.
- Emergency Preparedness: Drones might also tie into your business continuity and emergency planning in new ways. For instance, after a natural disaster, drones might be your quickest way to assess facility damage when roads are blocked. Or if there’s a chemical spill, a drone can sample the scene before sending people. As technology like gas sensors on drones or night-vision/thermal improvements come, consider them in emergency kits. Executives should incorporate drone capabilities into crisis management drills (“we will launch drones to get situational awareness in scenario X”). That way, the value is multiplied beyond security to overall resilience.
- Ethical Leadership: As you adopt advanced capabilities like AI surveillance or intercepting intruder drones, maintain a strong ethical stance. Use these powers judiciously and with oversight. It can be tempting to say “we have AI that can identify any individual on campus” – but ensure that’s tempered by privacy guardrails. Companies that overreach could face backlash or legal trouble. It’s wise to have an ethics or privacy officer review expansions to ensure they align with company values and societal norms. Being an early adopter means you set precedents – strive to set good ones. If you show that drones can be used responsibly at scale, it helps the whole industry and avoids prompting restrictive legislation from misuse by someone.
- Vision for Integration: Look at your overall corporate security strategy roadmap 5 years out and envision where drones fit in alongside other technologies (access control, cybersecurity, etc.). Many companies are pursuing convergence of physical and cyber security (Author: cuneosecurity – Cuneo Consulting). Drones could, for example, respond not just to physical alarms but to cyber incidents (imagine a scenario where an IT breach triggers concern that someone inside might be involved, and a drone is dispatched to surveil key areas for rogue insiders). These cross-domain uses might seem futuristic, but planning for convergence will make your security posture more unified.
- Environmental and Social Considerations: As future thinkers, also consider the environmental impact (drones are electric and relatively low energy – a plus; if replacing patrol vehicles that burn fuel, you can tout that sustainability win). Also consider community relations: maybe by the time you operate multiple drones, you invite local community reps to see the operation and understand you’re not spying on them – being open can prevent misunderstandings as the general public sees more corporate drones overhead.
By taking these steps, you ensure your investment in drone surveillance remains a strategic asset and doesn’t become outdated or outpaced by threats. In effect, you’re building a future-ready security ecosystem where drones (and counter-drones) are integrated, intelligent, and adaptable.
Conclusion: Partnering for Advanced Security
Drone surveillance has emerged as a powerful extension of corporate security, offering capabilities that traditional methods alone cannot match – from rapid aerial response and comprehensive coverage to data-driven insights. Over the course of this resource, we’ve seen how integrating drones into your security strategy can yield tremendous benefits: faster response times to incidents, broader situational awareness, cost efficiencies in patrol operations, and a strong deterrent effect against intrusions. We’ve also navigated the complexities – ensuring regulatory compliance with aviation rules, respecting privacy and ethical considerations, training your team and developing solid SOPs, and planning for the exciting advancements on the horizon like AI and autonomous swarms.
Implementing and sustaining such an advanced program is no small endeavor. It involves a blend of specialized knowledge, cross-functional coordination, and continuous adaptation. This is where choosing the right security partner makes all the difference. Cuneo Consulting stands ready to be that partner in your journey toward cutting-edge corporate security. As a state-licensed security firm with deep expertise in advanced technology integration, we bring both technical know-how and strategic insight to help you get the most from drone surveillance while avoiding pitfalls. Our team has experience in developing holistic security solutions – we understand not just drones, but how they dovetail with cameras, access control, and manned guard forces into a unified defense. We can assist at every stage, whether it’s conducting a feasibility study and ROI analysis for your particular sites, training your security staff in UAS operations, helping draft tailored SOPs and privacy policies, or integrating the live drone feeds into your existing command center platforms.
Most importantly, as the landscape evolves, Cuneo Consulting stays at the forefront of industry trends – be it new FAA regulations, emerging counter-drone tactics, or AI analytics innovations – so you don’t have to navigate those changes alone. Our consultants can periodically audit and update your drone program, ensuring it remains compliant with the latest laws and leverages the best available technology. In an era of rapid change, having a knowledgeable partner is like having a seasoned co-pilot for your security operations, keeping you on course no matter what.
By partnering with Cuneo Consulting, you gain a force multiplier not only in the form of technology but also in expertise and support. We treat your security objectives as our own mission. From day one of planning to full deployment and beyond, we work closely with your C-suite, Security Directors, Compliance Officers, and Operations Managers to align the drone program with your business goals and risk profile. The result is a seamless implementation that delivers robust security improvements – often exceeding expectations as seen in our previous client engagements – with minimal disruption to your operations.
In conclusion, integrating drone surveillance into modern corporate security strategies is not just about acquiring new gadgets; it’s about embracing a proactive, intelligence-driven approach to protecting your people, assets, and reputation. The “unblinking eye” of a well-run drone program provides confidence that your security team can see and respond to threats as they unfold, rather than after the fact. It exemplifies the forward-thinking mindset that top organizations use to stay ahead of risks. As you consider the next steps for enhancing your corporate security, we encourage you to reach out to our team for a consultation. Let us help you assess your needs, craft a solution, and guide you through implementation – so you can quickly reap the benefits of this technology while avoiding trial-and-error learning curves.
Secure the future of your corporate security program today. Contact Cuneo Consulting for expert guidance on deploying drone surveillance as part of an advanced, integrated security strategy. With our partnership, you can confidently elevate your security posture to new heights – literally – and ensure that your facilities are guarded by the very best in modern security innovation. Together, we’ll ensure that your organization remains safe, resilient, and ready for whatever challenges the future holds.
(For more information or to schedule a consultation, please visit our internal link: Cuneo Consulting Contact Page to get in touch with our security technology experts.)